Security and compliance are the most common terms in today’s businesses. The emerging risks of cyber threats make security and compliance essential to protect businesses. We used to mention these two concepts in the same breath, but they have distinct approaches. For quick understanding, security is the process of defending the invaders. At the same time, compliance is the laws that uphold your business and improve the business’s reputation. Thus, together, both can create a dynamic alliance that accelerates business growth.
The common question arises: why are the requirements aligned if security and compliance are two different aspects? You need to read the article to learn more about security vs. compliance. Then, you will understand how the two processes are alike and different.
UNDERSTANDING THE CONCEPT OF SECURITY
Security includes all your organization’s essential moves to defend against cyber threats. Therefore, simple security measures cannot protect your company against the risks. You must execute hardware and software security controls to prevent cyber attacks. In this regard, you can consider firewalls with multi-factor authentication to prevent unauthorized access. Cybersecurity provides a shield to your organization against cyber threats. Let’s discuss some common categories for security tools:
IT Infrastructure: This category includes all your organization’s computing systems. It protects the internet connection, firewalls, servers, data centers, and cloud computing systems. Software components secure operating systems, antivirus, and antimalware. Thus, security measures secure your data and prevent cyber threats.
Network Access: It is the most significant part of your organization from which attackers can infiltrate your systems. Therefore, strong passwords to firewalls and strategic restrictions in the company’s network can prevent risks. In this regard, Identity Access Management (IAM) tools ensure network security.
Authentication: Security starts with the authentication process, which provides an extra protection layer. Hence, two-factor authentication or multi-factor authentication can support this security measure. It prevents unauthorized access to secure servers, which is essential for security.
User Training: Human errors play a crucial role in information security incidents. Thus, proper employee training creates awareness of how to respond to phishing attacks or maintain cybersecurity cleanliness. The process may sound simple, but it profoundly affects managing and preventing cyber risks.
EXPLAINING THE CONCEPT OF COMPLIANCE
Compliance is rules and commitment to creating trust for your business. Therefore, it offers evidence and ensures the clients regarding security measures. In addition, compliance elevates the client’s confidence about the safety and security of their data. The application of security controls helps your organization in achieving compliance. However, the security measures can be industry-specific, similar to the compliance process. Suppose a healthcare industry requires the implementation of security controls for HIPAA compliance. At the same time, a SaaS-based company needs different security controls for SOC 2 compliance.
Furthermore, your organization can get compliance certification after implementing security controls. Compliance certification denotes that the companies meet regulatory demands. Consequently, you must remember compliance certification has strict renewal and surveillance audit deadlines. In addition, complying with proper compliance convinces clients that their data is safe. The most important reminder is that compliance ensures cybersecurity but does not guarantee protection against cyber attacks. The process of compliance requires continuous auditing and monitoring to fix security errors.
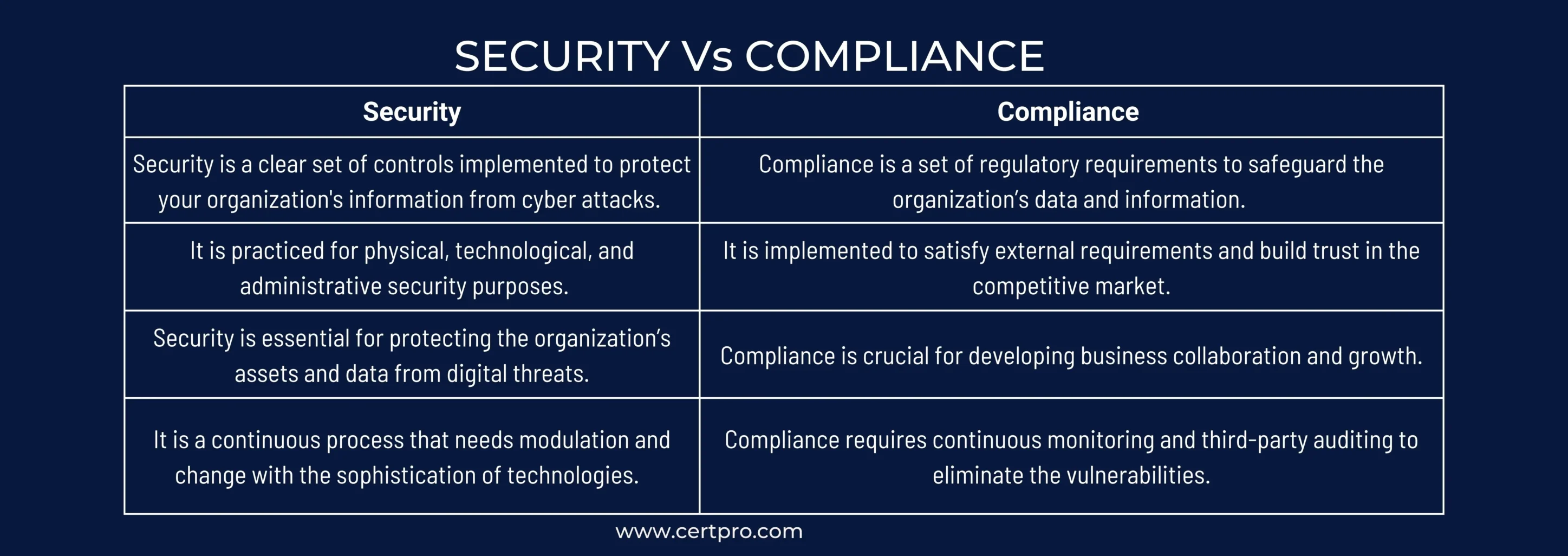
SECURITY VS COMPLIANCE
Security and compliance are interconnected but differ in key aspects. Again, security is a combination of controls to protect your organization’s assets. In contrast, compliance is meeting regulatory standards to satisfy legal requirements. Therefore, companies can secure their data by implementing standard compliance like GDPR, HIPAA, SOC 2, and ISO 27001. In addition, when your organization executes security controls to become compliant, your firm automatically follows the regulations.
Moreover, security and compliance are essential tools for risk assessment. Security measures and compliance needs must be aligned to achieve complete protection. In some cases, organizations implement security measures that are insufficient for compliance. For instance, an organization implemented antimalware, but the employees do not know the National Institute of Standards and Technology’s guidelines. Another example is an organization that implemented PCI DSS compliance but did not use the authentication tools for data access. It may create security gaps in organizations and increase vulnerabilities. Therefore, you should know security needs beyond compliance and have robust IT control covering all business areas.
SIMILARITIES OF SECURITY AND COMPLIANCE
Security and compliance are two common factors in cybersecurity. Hence, security measures are driven by business risk and legal obligations to implement compliance. Compliance helps to convince customers about their data security and privacy. Most importantly, with compliance certifications, the customers can understand what security controls the organizations apply. However, being compliant do not ensure security. Thus, you must understand how to mitigate and transfer risks to protect your system against threats. Hence, security provides well-protected and compliant communication for your clients.
Security measures are developed to protect the organization’s assets and prevent unauthorized access. Thus, organizations can implement different frameworks for their functionality and cybersecurity. Therefore, the compliance process can help organizations improve security by creating a specific standard and checklist. For example, your organization is implementing ISO 27001:2022 to develop a robust Information Security Management System (ISMS). However, your company is a SaaS provider and implements compliance for data security. In other instances, different IT companies can follow the exact compliance to create robust security controls.
Likewise, SOC 2 compliance creates trust for SaaS companies regarding data safety and security. In this process, the third-party auditor scrutinizes the data handling practices and ensures protection. Therefore, SOC 2 compliance assures customers that their data is appropriately managed.
STATISTICAL ANALYSIS OF DATA SECURITY AND COMPLIANCE
Security controls and compliance are constantly evolving due to emerging risks. Let’s check out some insightful data on the cost of data breaches in recent years and determine the relevance of security and compliance for your organization.
It is a known fact that data breaches and cybersecurity incidents negatively influence your business’s growth and development. The incident can cause financial, reputational, and operational difficulties. Statistical data suggested that cyberattack losses could reach $10.5 trillion by 2025. Therefore, a 300% high rise was observed from 2015. Interestingly, IT hacking incidents increased by 80% in 2022, which was around 45% in 2018. Thus, it indicates that technological advancement makes hackers more efficient. One company in every 31 companies worldwide experienced weekly ransomware attacks in 2023. The scenarios suggested that businesses require cybersecurity measures to continue their business and functionality.
Today, we live in a fast-paced world where technology is improving regularly. Thus, it signifies that hacking technologies are also advancing and extending. Again, businesses face more cyber threats, which create pressure on implementing security compliance. However, organizations should take proper measures to maintain compliance. The data on implementing compliance suggested that 88% of global companies spend $1 million yearly on GDPR compliance, and 40% spend over $10 million annually. Cybersecurity risks frighten the world; therefore, around 250 bills and resolutions have been introduced to prevent cyber threats. As per many cybersecurity observers, privacy laws will protect the personal information of 75% of people worldwide by the end of 2024.
CERTPRO’S GUIDANCE IN SECURITY AND COMPLIANCE
CertPro knows that compliance is a roadmap, and security is the journey. On this road, you cannot take a break; you need to keep upgrading your security measures and inform your target audience about your precious movement. Our experience and knowledge can help you beyond the basic process.
CertPro can guide you on the path to security and compliance. Our risk assessment team can help your organization implement a robust framework in cybersecurity. We can analyze your organization’s needs and design a security posture. In addition, our expert guidance and help can improve your confidence and market reputation. We offer customized services for our clients by following the compliance checklist and meeting our client’s demands. You can visit CertPro.com to understand cybersecurity and compliance. Contact us for more detailed and tailored queries; our executives will help you with this request.
FAQ
What is the role of security compliance?
What is a breach of security in data protection?
What are the types of security breaches?
How to report a data breach?
What are the primary security requirements?

About the Author
Anuja Patil
Anuja Patil, an Executive Team Lead at CertPro, excels in guiding her team to deliver premier information security solutions. With a strong background in ISO 27001, SOC2, GDPR, and various other compliance standards, she ensures that projects are managed efficiently and security frameworks are continually optimized.
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...
BUSINESS NON-COMPLIANCE: THE HIDDEN FINANCIAL AND OPERATIONAL COSTS
Businesses are always in a dilemma regarding whether or not to be compliant. Most companies think that compliance will problematize their operating process. However, highly regulated industries like financial and healthcare services meet the legal obligations for...
Security Frameworks: A Comprehensive Guide with 14 Examples
Technological advancements make cyberattacks more sophisticated and advanced. Hence, organizations must keep up with the latest cybersecurity frameworks in these complicated scenarios to sustain themselves in a dynamic threat environment. Different cybersecurity...




