In today’s businesses, the value of information is no less than any asset a company possesses. However, consecutive cyberattacks and threats disturb the collecting and storing process of information. Thus, the incident of emerging cyber threats enhances the risk to information security and makes the company vulnerable to cyberattacks. In this regard, organizations must have a robust security protocol to eliminate threats and maintain a safe environment.
The concept is not as simple as you think. The complex operational process and modern technologies make risk more complicated and challenging. Most organizations agree that risk becomes convoluted with time. Thus, the existing risk assessment techniques are inadequate to address the threats. Along with the technologies, cross-sector collaboration increases business risks. In addition, cloud risks are becoming more complicated, according to cyber risk professionals.
This article will discuss infosec risk management in 2024 and how to manage the complex risk environment with proactive strategies.
UNDERSTANDING THE INFOSEC RISK MANAGEMENT
Information Security Risk Management(ISRM) helps companies identify vulnerabilities and create mitigation strategies. The process manages the risks associated with information security. In detail, it helps to identify, assess, and treat the risks to maintain data security, integrity, and confidentiality. Furthermore, the ISRM treats risks based on the organization’s risk tolerance. A standard advice is that businesses should not try to eliminate the risks; organizations should identify them and achieve a risk mitigation strategy.
Moreover, the risk management program addresses business uncertainties and ensures the desired business outcomes are achieved. However, risk management is not constant; it is modified per the organization’s size and functionality. Here we mention some benefits of risk management for your businesses:
- Recognize the vulnerabilities of an information system.
- Identify the extent of vulnerability and its possible impact on your organization.
- Evaluate the cost, probability of occurrence, and impact on your organization to determine the best ways to manage risks.
- Provide opportunities for organizations to develop proactive strategies in risk management.
- Offer a systematic way for organizations to identify and manage potential threats and vulnerabilities.
CORE COMPONENTS OF EFFECTIVE RISK MANAGEMENT
Effective risk management requires a few considerations to eliminate the risks and keep the process moving:
Risk Inventory: Organizations must have a comprehensive inventory of assets and related risks. Thus, scoring risks helps you understand the importance of potential threats and implement necessary controls to eliminate the threats.
Clear Ownership: Combating risks involves taking appropriate measures at the correct time. Thus, transparent ownership of risks and related actions should be documented. It will offer you a transparent picture of the organization’s infosec risk management process.
Align Controls with Compliance: Organizations must implement risk management controls that align with compliance best practices. This helps develop a robust framework for the overall risk management process.
Continuous Monitoring: Risk monitoring helps identify risks in the compliance process and identify gaps in the controls.

RESPONSIBILITIES IN MANAGING INFORMATION RISKS
The best risk management plans can be insufficient for your organization if communication is inconsistent. Thus, a successful risk management program depends on the stakeholder’s participation.
Process Owners: These high-level players are usually the finance or audit team in charge of the ERM (Enterprise Risk Management) program. The information security team oversees the ISRM program, which is part of ERM. Therefore, people on this team need to be in the field constantly to move the process forward.
Risk Owners: These people fix certain risks in their systems by buying the tools needed for mitigation, tracking, and repairing the process. Therefore, the risk owner is responsible for managing the risks. Thus, you will be the risk owner if you accept the budget for any risk management project.
Information Security Risk Management Team: This group will implement the chosen treatment plan. It includes system users and system managers or engineers. The management team is in charge of the parts of the risk management method related to computers and securities.
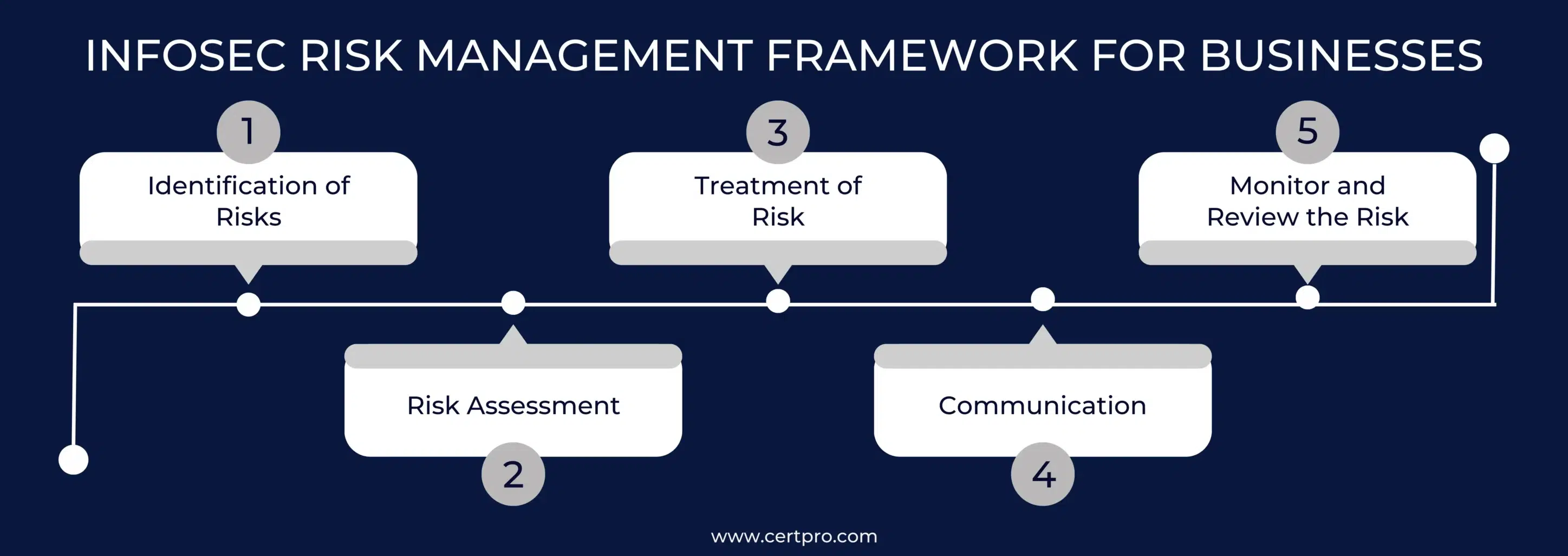
INFOSEC RISK MANAGEMENT FRAMEWORK FOR BUSINESSES
Infosec risk management is a systematic approach to managing risks and preventing data breaches. The following points can help you in creating a framework for managing the information security risk in your organization:
Identification of Risks: The first stage of the risk management framework helps identify your organization’s risks. Therefore, it identifies assets relevant to information security that impact an organization’s integrity and confidentiality. The risks may relate to the network, servers, and devices. In addition, the identification of vulnerabilities is also essential for risk management. It can put the organization in a vulnerable position. Therefore, weak passwords, lack of encryption, and poor data backup increase the risks.
On the other hand, identifying potential threats in risk management helps manage risk appropriately. It helps to understand possible threats from vulnerabilities and their impact on your organization. Threats can arise from software, malware, and infrastructure failures.
Risk Assessment: The next step is to review the risks, which assess the occurrence of risks and its impact on your organization. Therefore, risk assessments help businesses identify the most impactful risks for businesses.
Treatment of Risk: The risk assessment process identifies potential risks, and organizations must select the treatment process. One option is remediation, where controls are implemented for specific instances to fix the vulnerabilities. On the other hand, mitigating risks reduces the likelihood and impact of risks on businesses. However, it can not fix the vulnerabilities. Another risk treatment is a transference of risk, in which you can purchase insurance coverage from a third party to cover the cyber losses. However, organizations can purchase such opportunities through risk mitigation strategies and remediation processes.
Furthermore, risk acceptance is a treatment process in which risk management may cost more than the incident. In this situation, ensure the process does not affect the other function and keep it untouched. Lastly, risk avoidance is a treatment process; you can change or remove the data from the affected servers or places. Basically, it avoids the risks by transferring the data to a safe environment.
Communication: No matter which treatment choice you make, the employees need to know about it. Thus, the employees should be involved in the process and make them realize the importance of security practices in your organization. In addition, accountability and duty should also be clearly outlined and linked to specific people in the organization. During incidents, inform the concerned person and take appropriate measures. In this regard, the IT team will prevent the reoccurrence of the incident and preserve the environment.
Monitor and Review the Risk: Risk management is an ongoing process. Therefore, continuous security tracking and upgrading procedures ensure the organization’s systems are always safe. Thus, the risks should be checked often, especially when a system, purpose, vision, or process change occurs. You can also look at risks again during modifications to rules and regulations.
CHALLENGES WITH THE TRADITIONAL RISK MANAGEMENT PROCESS
The traditional risk management process has some issues that can be eliminated with the automation of risk management programs. The common problems are:
Broad-Brush Approach: Comprehensive risk management requires an inclusive view of risks. This approach creates challenges because time, resources, and budgets are limited. It often forces organizations to consider all risks equally or overestimate their importance. Therefore, the consequences of susceptible risk can cause massive damage to companies.
Insufficient Risk Assessment: A periodic risk assessment will be inadequate in a volatile market where new threats are constantly multiplying. In many cases, manual risk assessment may cause errors in risk-finding. Thus, the risk can penetrate the gaps and manipulate your organization’s security posture. Therefore, continuous monitoring is essential to find vulnerabilities and fix errors in this scenario.
Illusion of control: The traditional risk management process usually ends with listing risks, potential results, and ways to reduce those risks. However, eliminating vulnerabilities from the list does not help in preventing and managing risks. For that reason, businesses need to be able to evaluate and mitigate risks continuously.
FINAL THOUGHTS
An effective risk management program depends on assessing risks, communicating plans, and sticking to the process. The same steps can also be used to manage hacking risks. CertPro can help you find the gaps in your compliance process. We offer external audits for automated compliance facilities. Our expert auditing team will collaborate with your compliance partner to continue the audit process. In addition, our cybersecurity audit team will guide you and help you continue the compliance journey.
FAQ
Is ISO 27001 a risk management framework?
The risk assessment and management are critical steps in your ISO 27001 certification. In fact, an organization-wide risk assessment is the central focus of ISO 27001.
Is ISO 31000 a risk management framework?
The standard describes a risk management process that establishes the organization’s framework and principles for risk management.
What are the three significant types of IT risks?
The risks can be categorized as IT security, hardware or software failure, and IT disasters.
What is cyber security risk?
Cybersecurity risk is the potential for exposure or loss from a cyberattack or data breach. Thus, it involves identifying potential threats and vulnerabilities in your organization’s digital network systems.
What is the difference between ISO 27001 and ISMS?
ISMS is a systematic approach to managing and protecting sensitive company information. ISO 27001 is an international standard that provides requirements for implementing and certifying an ISMS.

About the Author
Anuja Patil
Anuja Patil, an Executive Team Lead at CertPro, excels in guiding her team to deliver premier information security solutions. With a strong background in ISO 27001, SOC2, GDPR, and various other compliance standards, she ensures that projects are managed efficiently and security frameworks are continually optimized.
TOP 9 RISK ASSESSMENT TOOLS FOR BUSINESSES IN 2024
Risk assessment helps organizations strengthen their security posture and recognize potential risks to their compliance processes. It also evaluates the severity of the risk and minimizes its impact on business operations. In addition, risk assessment tools are...
COMPLIANCE RISK MANAGEMENT: EXPERT STRATEGIES AND BEST PRACTICES
Compliance risk considers the organization's potential legal, material, and financial losses due to compliance failure. Thus, compliance risk is known as integrity risk. Organizations of all sizes are exposed to compliance risk. Hence, compliance failure results in...
TOP 7 DATA LOSS PREVENTION STRATEGIES IN 2024
In the contemporary business landscape, data is the cornerstone of organizational vitality. Businesses leverage data extensively to inform decisions, maintain competitiveness, and foster expansion. Nonetheless, they encounter multifaceted challenges emanating from...