Technological advancements make cyberattacks more sophisticated and advanced. Hence, organizations must keep up with the latest cybersecurity frameworks in these complicated scenarios to sustain themselves in a dynamic threat environment. Different cybersecurity frameworks are available to protect your organization from specific cyber threats and mitigate potential vulnerabilities. Thus, a common security framework is sufficient to create a digital defense for your organization.
In this context, entrepreneurs understand the importance of cybersecurity well, but sometimes, the process can be daunting and stressful. Hence, you realize the need for a framework but need help understanding what should be considered. This article will explore the 14 common security frameworks specific to the industry’s needs. The article might help you in choosing the correct framework for your organization. Read the article to learn more about your business’s common security framework.
WHAT IS A COMMON SECURITY FRAMEWORK?
A security framework signifies policies and procedures for developing and maintaining an organization’s security controls. A common security framework defines a process commonly used to protect an organization from cyberattacks. In brief, a security framework offers guidelines that organizations must follow to mitigate cyber threats. Hence, the framework provides a common language and standard for global security leaders. It creates an effective security strategy that meets the specific needs of the organizations. Further, the framework evaluates the gaps in the existing practices and implements a robust approach to protect the organization’s critical assets.
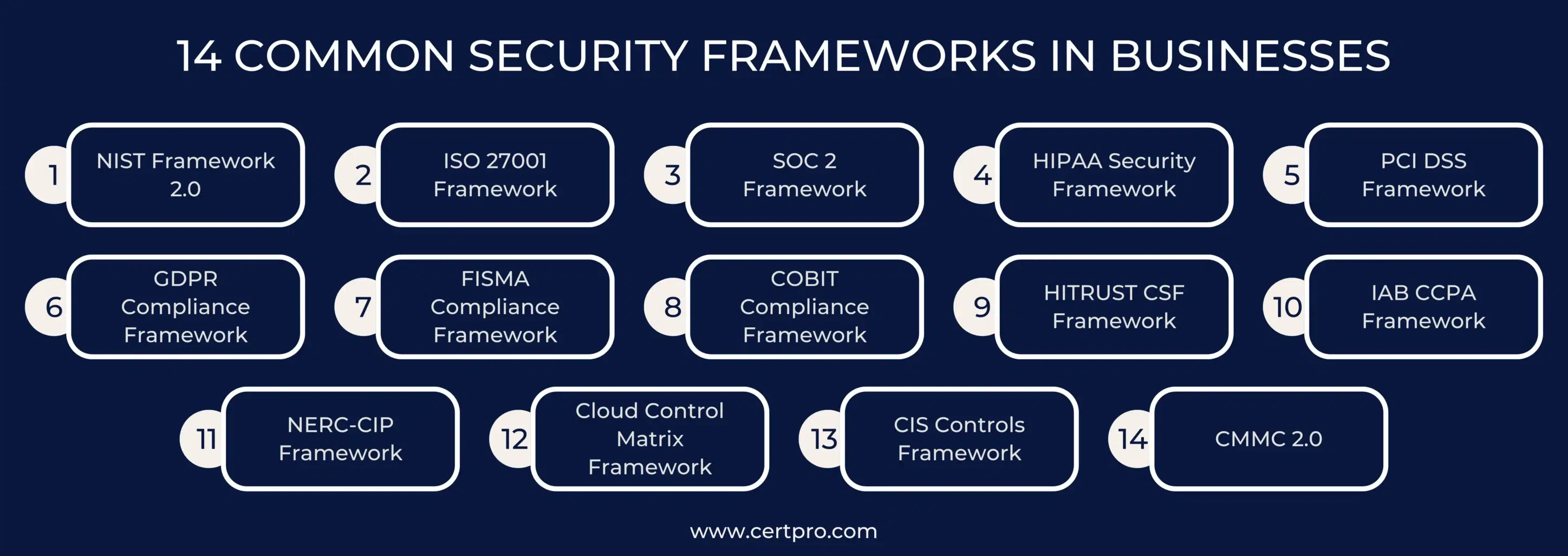
14 COMMON SECURITY FRAMEWORKS IN BUSINESSES
Appropriate security frameworks and solutions help organizations to sustain in the competitive environment. Here are some common security framework examples:
1. NIST Framework 2.0: It was established to collaborate between the public and private sectors to identify, assess, and manage cyber risks. In addition, it is a voluntary practice that improves an organization’s cybersecurity aspect. Thus, the concept defines an organization’s cybersecurity goals into five phases: identifying, protecting, detecting, responding, and recovering.
Applicable For: Any organization can apply the framework.
Core Focus: The framework helps identify comprehensive weaknesses in your organization.
Benefits: It helps businesses determine what assets and processes to protect, such as data centers and network entry points. This might also help prevent malware attacks.
2. ISO 27001 Framework: The International Organization for Standardization introduced it to provide guidelines for improving your organization’s information security. Thus, it offers reliability and trustworthiness among customers and stakeholders. Hence, an Information Security Management System (ISMS) is a tool for keeping information safe.
Applicable For: Organizations handling sensitive data can implement the framework.
Core Focus: Develop an organization’s Information Security Management System (ISMS).
Benefits: Achieving ISO 27001 compliance will improve the brand reputation and streamline the operational processes.
3. SOC 2 Framework: It is known as Service Organization Control Type 2. It is a cybersecurity framework developed by the American Institute of Certified Public Accountants. Thus, it helps manage and secure the client’s data. A common security framework like SOC 2 requires extensive auditing to get the final report. Therefore, its comprehensive auditing process makes SOC 2 one of the most rigid security frameworks to implement.
Applicable For: SaaS companies, financial sectors, and organizations handling customers’ data can use the framework.
Core Focus: The main aim is to achieve customer data management and third-party risk management.
Benefits: The compliance secures the safety and privacy of customer data and prevents the risk of data breaches.
4. HIPAA Security Framework: The Health Insurance Portability and Accountability Act (HIPAA) was developed in 1996 to ensure patient safety. Thus, healthcare organizations must conduct risk assessments and cybersecurity practices to comply with HIPAA rules.
Core Focus: HIPAA Compliance protects patient health information and reduces the risk of data breaches.
Benefits: HIPAA is a set of cybersecurity rules that informs healthcare organizations on how to keep electronic health information safe and private.
5. PCI DSS Framework: The Payment Card Industry Data Security Standard (PCI DSS) was established in 2006 to ensure that all businesses that take credit card information handle the data securely. Similarly, the main goal of the system is to protect cardholder data. Thus, any company that deals with this kind of information has to follow PCI DSS despite the organization’s standards.
Applicable For: Organizations managing and handling transaction information can implement compliance for their customer data security.
Core Focus: It secures the card owner’s information and prevents data linkage.
Benefits: Compliance provides a comprehensive measure to secure the functionality and prevent unauthorized access to customer data.
6. GDPR Compliance Framework: It is a common security framework to protect customer data in a specific region. Thus, the General Data Protection Regulation (GDPR) helps protect EU customers’ data. Hence, it covers all companies that gather and use data about EU citizens, whether based in the EU or elsewhere. Also, the framework has consumer data access rights, security rights, and consent rules.
Applicable For: Businesses that collect and handle data from EU citizens need GDPR compliance.
Core Focus: Compliance aims to manage data protection for EU citizens and prevent the unethical use of data.
Benefits: The GDPR affects all businesses based in the EU or that collect and store personal information about EU people.
7. FISMA Compliance Framework: The Federal Information Security Management Act (FISMA) is a complete cybersecurity framework that protects federal government systems and information from cyber threats. Therefore, this common security framework is similar to the cybersecurity standards set by NIST. Thus, agencies and third parties must track their digital assets and determine their safety.
Applicable For: It covers the federal government and outside groups that work for it.
Core Focus: The compliance aims to protect government assets from cyberattacks.
Benefits: FISMA requires the documentation of digital assets and network connections like NIST. Additionally, businesses must monitor their IT systems and assess risks and weaknesses regularly.
8. COBIT Compliance Framework: Control Objectives for Information and Related Technology was developed by the Information Systems Audit and Control Association in the middle of the 1990s. Thus, the framework lowers an organization’s technology risk by developing information management strategies. Since the 1990s, COBIT has been changed a few times to keep up with new security threats. Therefore, the most recent versions focus on ensuring that IT goals are aligned with business goals and risk management.
Applicable For: The security framework applies to publicly traded companies.
Core Focus: It aims to use technology to manage business goals, security, risk management, and information governance.
Benefits: COBIT also has specific rules for protecting and controlling data. These rules include managing access, authenticating users, and encrypting data. These rules give businesses a complete list of steps to keep their systems safe from cyber threats.
9. HITRUST CSF Framework: Even though HIPAA is an excellent way to protect against online threats, healthcare data breaches still happen far too often. Thus most of the healthcare companies do not have an incident response plan. Therefore, following the common security framework like HIPAA is not always enough. In that case, organizations can apply HITRUST CSF for more concrete solutions.
Applicable For: Any organization can apply the compliance, especially the healthcare sectors.
Core Focus: It enhances the security of healthcare organizations and technology vendors.
Benefits: This standard lists the best ways to keep patient data safe. Again, it manages identities and data access. In addition, it maintains audit logs, encrypts data, and responds to incidents.
10. IAB CCPA Framework: The Interactive Advertising Bureau California Consumer Privacy Act (IAB CCPA Compliance Framework) applies to California customers. Hence, the framework offers more power to Californians over their personal information. In addition, it requires companies that gather user data to comply with specific rules.
Applicable For: Organizations that manage California residents’ personal data need to comply with CCPA standards.
Core Focus: The compliance aims to protect California consumers’ data and give them authority over it.
Benefits: With this framework in place, Californians will have more control over their personal details. Thus, companies that collect information about users and ad tech companies that buy that information must follow certain rules.
11. NERC-CIP Framework: It is known as North American Electric Reliability Corporation Critical Infrastructure Protection. In the recent past, more attacks have occurred on critical U.S. infrastructures. Therefore, NERC CIP is a set of security standards to lower the cyber risk in the power sector and ensure the reliability of bulk electric systems. Hence, the NERC-CIP security framework helps businesses to identify and reduce cyber risks from third parties in their supply chain.
Applicable For: Organizations working with the North American energy grid can comply with the common security framework.
Core Focus: The CIP standards are a group of safety measures that keep the critical parts of the power grid safe from online threats. The guidelines cover many things, like power plants, transmission lines, and control centers.
Benefits: Keeping the utility infrastructure safe from cyberattacks. In addition, protect the necessary services like transportation, phone service, and energy from cyber threats.
12. Cloud Control Matrix Framework: The Cloud Control Matrix (CCM) from the Cloud Security Alliance (CSA) protects cloud-based systems and apps by controlling who can access them, ensuring users, encrypting data, keeping records for auditing, and responding to incidents. The CCM, like HITRUST, has specific rules for managing cybersecurity risks and ensuring that organizations follow regulators’ rules.
Applicable For: Cloud-based companies can comply with compliance.
Core Focus: The Cloud Controls Matrix is a tool for security experts and inspectors that provides information about domains. Thus, it aims to make private cloud systems safer by reviewing them for audits.
Benefits: The CCM can help companies find holes and ways to improvement. It ensures compliance with rules and regulations. In addition, it also monitors the effectiveness of security measures.
13. CIS Controls Framework: The main goal of most cybersecurity frameworks is to find and control risks. Thus, Center for Internet Security Controls, on the other hand, are just a list of things that any company can do to keep itself safe from online threats. Thus, data safety, audit log management, malware defenses, penetration testing, and other things are all examples of controls.
Applicable For: Any organization can apply the compliance.
Core Focus: It offers general protection against cyber threats.
Benefits: Basically, other systems are great for finding the vulnerabilities in the systems.
14. CMMC 2.0: The US Department of Defense (DoD) confirmed in 2021 that CMMC 2.0, or Cybersecurity Maturity Model Certification, is the newest version of its framework. The goal was to protect national cybersecurity information by giving all organizations that work with the DoD the same set of cybersecurity rules.
Applicable For: It applies to organizations that handle Federal Contract Information (FCI) or work with DoD.
Core Focus: CMMC requires companies with access to national security information to follow cybersecurity guidelines.
Benefits: The program aims to keep private data safe, implement high standards, and ensure everyone is responsible for handling sensitive information.
SECURITY FRAMEWORK ESSENTIAL FOR YOUR BUSINESSES
We explore the most common security frameworks for your business. Multiple types of cybersecurity frameworks makes you confused and you are probably wondering which apply to your business for better results. Thus, common security frameworks can clarify which security controls organizations should implement to safeguard the data. However, compliance is a complex process that needs professional guidance and help. Hence, CertPro can streamline the process by providing thorough compliance audits and suggestions against the most in-demand frameworks. We offer the best services on SOC 2, ISO 27001, HIPAA, PCI DSS, GDPR, and more. Again, you can get quality services at an affordable rate. For more details, visit our website, CertPro.com, and take personalized help and suggestions.
FAQ
What are the 5 basic security concepts?
The basic concepts are confidentiality, integrity, availability, authentication, and non-repudiation.
What are the 3 types of software security?
It includes protection of software in general, portection of data processing software, and protection of communication systems of organizations.
What is a security risk framework?
A cyber risk management framework can help organizations effectively assess, mitigate, and monitor risks; and define security processes and procedures to address them.
Why are security frameworks important?
A security framework lays out the rules and steps for setting up and keeping up security controls. Clearing up the steps used to keep a business safe from cyber threats.
What is a mitigation step?
Mitigation refers to the steps that can be taken prior to the event to reduce adverse and potentially long-term effects.

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...
BUSINESS NON-COMPLIANCE: THE HIDDEN FINANCIAL AND OPERATIONAL COSTS
Businesses are always in a dilemma regarding whether or not to be compliant. Most companies think that compliance will problematize their operating process. However, highly regulated industries like financial and healthcare services meet the legal obligations for...
WHAT IS GRC AUDIT?
In modern businesses, GRC is essential for upgrading the existing compliance practice. Thus, GRC meaning signifies governance, risk, and compliance which manage risks. The GRC audit helps to optimize the processes and controls of industry-specific regulations....