IT compliance is essential for every organization to secure the integrity and accountability of data. The process also helps develop the business and enhance its profitability. In today’s digital era, IT compliance has more than just a regulatory checkbox. It plays a crucial role in your organization’s risk management strategy. Consequently, organizations face intensified pressure to achieve complex compliance standards with time. The proliferation of remote work, cloud-based business models, and artificial intelligence makes maintaining compliance difficult. In addition, new data privacy regulations and laws make compliance requirements more complex. Organizations feel pressure to maintain compliance and avoid the consequences of non-compliance. Now, businesses need to stay ahead in compliance practices to prevent the risk of falling behind.
This article delves into IT compliance and outlines its importance, providing a checklist to help you understand the whole idea. Read the article to avoid potential compliance issues in your organization.
WHAT IS IT COMPLIANCE?
IT compliance signifies that businesses meet all legal requirements regarding data and computer systems. This process involves using technology to comply with the rules and laws that affect your business. For instance, if you run a financial services company, there are rules about how you can handle information about your customers and how you run your business. Thus, it fixes rules for operating your company’s digital systems and determines compliance requirements. This IT requirement needs to keep private information safe, ensure the safety of computer network links, and use technology that follows the organization’s rules and laws. Hence, companies that violate the compliance requirements suffer hefty fines and reputational damages.
DIFFERENCE BETWEEN IT COMPLIANCE, DATA PROTECTION, AND IT SECURITY
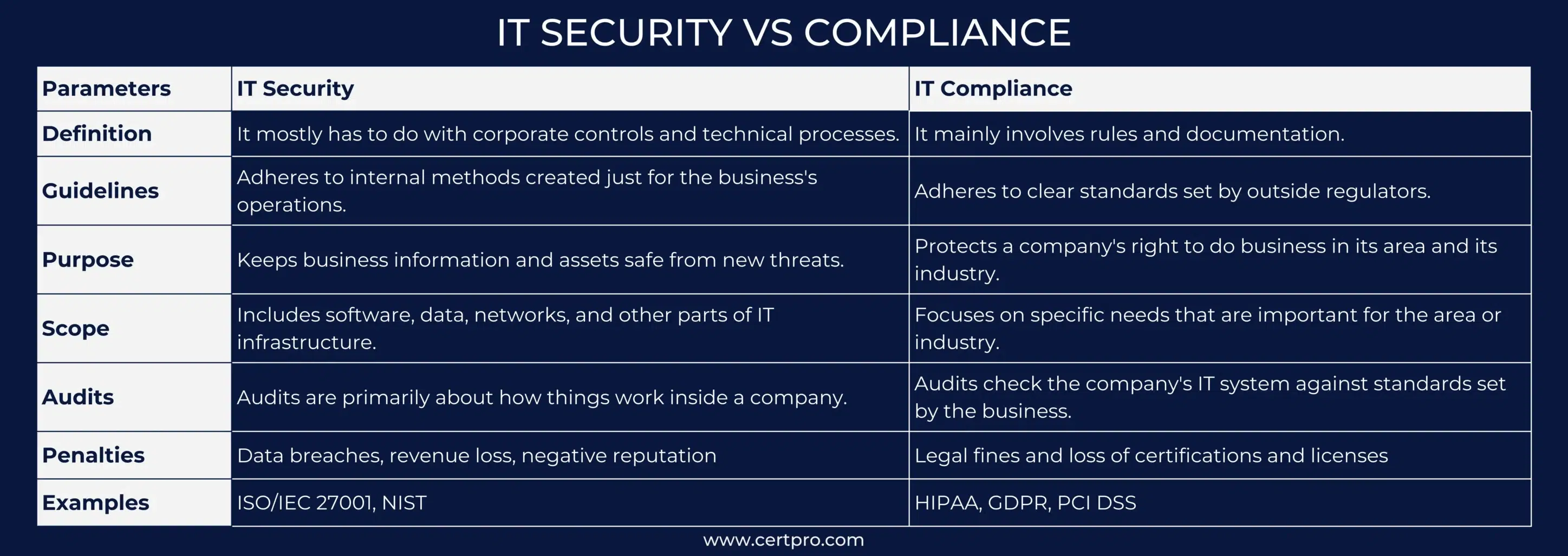
Sometimes, we misunderstand IT compliance with data protection and IT security. However, IT security and data protection help implement technologies to protect data and information. At the same time, IT compliance deals with adherence to compliance requirements and provides data security and protection in your organization. On the other hand, IT security and data protection are not limited to compliance. The regulatory requirements are based on your organization’s principles. Thus, companies can avoid implementing specific solutions to secure their IT. However, organizations must implement solutions to comply with the industry-specific regulations. Further, the main aim of compliance is to ensure a secure system and transparent process.
TYPES OF IT COMPLIANCE STANDARDS
The data storage affects the compliance standards that monitor business operations. There may be more than one set of rules that an organization must follow. Here are some of the most popular ones:
HIPAA Compliance (Health Insurance Portability and Accountability Act): HIPAA requires healthcare providers to secure customer information. Thus, Healthcare industries that deal with patients’ personal information need a HIPAA solution. Some important parts of HIPAA are:
- Covered entities cannot share Protected Health Information (PHI) about patients without their permission.
- Encryption and access control must be in place to keep electronic PHI safe and secure.
PCI-DSS (Payment Card Industry Data Security Standard): Organizations working with credit cards and online payments must comply with this act. This IT compliance protects cardholder information and reduces the risk of fraudulence. Again, some important considerations are :
- When data is sent over public networks, it must all be encrypted to keep it safe. In addition, system security must be tested and updated often.
- Organizations must use firewalls and regularly update the security software to ensure safety.
- Only authorized persons must be able to view cardholder data inside an organization. Thus, people with sensitive data access should be given unique IDs.
SOC (Systems and Organizational Controls): Cloud-based organizations must follow SOC standards and audits to ensure data security and privacy. The AICPA developed SOC standards and audits as a voluntary data protection compliance for service organizations. Important considerations are :
- It has five trust service criteria that ensure data security, privacy, confidentiality, integrity, and availability.
- Implementing strong administrative and technical controls prevents unauthorized access to customer’s data.
SOX (Sarbanes-Oxley Act): SOX regulates how companies handle computer records, data security, internal reporting, and executive responsibility. Since 2002, this compliance standard has required companies to provide complete and correct financial information. Some important SOX rules are:
- Organizations must provide an accurate financial report.
- An internal auditing team must be created to ensure the integrity of financial reports.
- The external auditor will review the internal financial systems and prevent the risk of financial fraud.
GDPR (General Data Protection Regulation): Its goal is to protect the rights of EU members and keep their data safe. All companies that handle the personal information of people living in the EU must follow these strict rules, no matter where they are located. Some of the essential rules are:
- You must get their explicit permission before collecting and using customer information. Consent should also be easy to withdraw. Individuals have the right to request data corrections and deletions from records.
- Companies must inform the authorities and affected individuals within 72 hours of discovering a data breach.
LATEST TRENDS OF IT COMPLIANCE
Some changes have been observed in the IT compliance process in recent years. It has a substantial impact on businesses and their functionalities. Let’s discuss the trends in brief:
- As for changes to regulations, 2024 will see the use of AI in regulatory compliance, with the implementation of AI-driven tools that aid in risk assessments, compliance tracking, and decision-making.
- The Global Reporting Initiative (GRI) or the Sustainability Accounting Standards Board (SASB) will become more important in 2024. Hence, businesses that want to be sustainable will use these frameworks.
- It utilizes Regulatory Technology (RegTech), Cloud Computing for GRC Scalability, Internet of Things (IoT), Real-Time Monitoring techniques, and Blockchain technology to handle real-time regulatory monitoring effectively. Thus, businesses must adapt and uphold the most recent regulatory changes in 2024.
WHY IS COMPLIANCE IMPORTANT?
IT compliance is substantial because it ensures businesses follow the law and regulations, keep data safe, and handle risks well. Thus, risk management is also a part of compliance, including tools like risk assessments and mitigation of risks. This lets organizations find and reduce possible threats, which ensures total safety and long-term business continuity. Here, some other importance are listed below:
- Compliance can protect private business data, lower the risk of breaches, and ensure internal and client data availability.
- It also leads to efficiency, a competitive edge, and uniformity worldwide.
- Compliance avoids fines, penalties and protects the organization’s reputation. .
- It creases confidence in development and growth by attracting and retaining customers.
- The process offers efficient data management and higher-quality partnerships.
WHO REQUIRES COMPLIANCE?
All private businesses, government agencies, and other groups must follow compliance rules. The needs of compliance vary depending on the industry, the size of the business, and the number of customers. Thus, critical infrastructure in energy, healthcare, government and administration, food, transportation, finance, and insurance requires compliance. Some other important industries for strict compliance practices are IT, telecommunications, media, and culture.
Further, complying with rules can be so complicated, especially in large businesses, that compliance management staff must perform it correctly. Consequently, companies are even expected to show regularly that they are meeting all IT compliance requirements. Thus, reports from external auditors and penetration tests are examples of how companies can achieve this.
WHAT IS COMPLIANCE RISK?
Compliance risk is losing money because of failing a compliance check. This could include civil penalties and money lost from fines or fees. Therefore, loss of customer trust, poor brand image, and reputation damage from a data breach or leaked customer information are all examples of IT compliance risk.
How to lower the risk in your organization:
- Find out what internal and external factors affect your company’s compliance.
- Keep your company updated on changes to industry frameworks and compliance standards.
- Ensure your organization’s tools, methods, and procedures follow policies and best practices to help you reach your goals.
- Plan how compliance and security will work together and maintain corporate compliance.
To address today’s complicated needs, businesses must find a balance between meeting their market’s privacy and security needs and ensuring that policy enforcement and compliance can grow and last.
WHAT IS IT COMPLIANCE CHECKLIST?
Specific compliance requirements depend on the standard and industry, but a successful IT compliance program must have these key parts:
Assess Risk: Review your IT systems and processes regularly to find regulatory risks and holes.
Implement Policies: Ensure your employee knows the crucial compliance rules and their vital role by holding regular training and awareness programs.
Review Controls: Use MFA, role-based access controls, and frequent access reviews to ensure that only authorized people can access sensitive data and systems.
Data Loss Prevention: Compliance standards for disaster recovery require your company to have robust backup and recovery systems in place so that infrastructure breakdowns have as minimal an effect on your business as possible.
Encryption and Data Protection: When sensitive data is sent or stored, it should be protected from unauthorized access to avoid data manipulation. Thus, data encryption ensures your organization’s secure handling of sensitive data.
Incident Reporting: Develop a plan for finding, investigating, and handling possible incidents. Include ways to report security breaches to the right people and groups.
Continuous Monitoring: Monitor your IT compliance systems and processes to recognize vulnerabilities and conduct regular compliance audits to assess the effectiveness of your program.
Endpoint Visibility: If you can see the state of your compliance in real time, you can find and fix potential compliance problems before they worsen. Hence, it strengthens your security posture in many ways.
START YOUR IT COMPLIANCE WITH CERTPRO
It may seem impossible to achieve IT compliance, but the reality is different. An actionable plan is often the first step toward your compliance journey. That means examining your company and infrastructure and being honest about where you are most at risk. Following that, learn about the rules and regulations for compliance in your business. Finally, implement your plan to ensure that the systems, processes, and methods you use daily uphold those standards.
CertPro can help you whether you are just starting your compliance journey or want to maintain or improve your compliance practices. As a consultant, CertPro can help you determine where you are most vulnerable and set up controls to help your company stay compliant. For more precise help, connect us through CertPro.com, we are happy to help.
FAQ
What does it mean to be IT compliant?
Being IT compliant means that an organization meets all legal and regulatory requirements related to its data and computer systems, ensuring that operations adhere to applicable rules.
What areas does IT compliance cover?
IT compliance encompasses various aspects, including software, data, networks, and overall IT infrastructure, focusing on adhering to specific industry regulations and standards.
How does IT contribute to compliance efforts?
IT plays a critical role in compliance by implementing technologies and processes that ensure adherence to laws and regulations, safeguarding data security and privacy.
How does IT compliance differ from data protection and IT security?
IT compliance focuses on meeting regulatory requirements, while data protection and IT security involve implementing measures to safeguard data and systems. Compliance ensures adherence to legal standards.
How can organizations lower compliance risk?
Organizations can lower compliance risk by regularly assessing risks, keeping updated on regulations, implementing robust policies, and ensuring continuous monitoring and incident reporting systems.

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
POLICY MANAGEMENT SYSTEM: ESSENTIAL TOOLS FOR AUTOMATION AND SIMPLIFICATION
Growing businesses indicates that you become a master in your field and accurately manage all business-related policies. However, managing company policies can be daunting significantly when your business expands. Here, an effective policy management system can help...
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...
BUSINESS NON-COMPLIANCE: THE HIDDEN FINANCIAL AND OPERATIONAL COSTS
Businesses are always in a dilemma regarding whether or not to be compliant. Most companies think that compliance will problematize their operating process. However, highly regulated industries like financial and healthcare services meet the legal obligations for...




