Risk assessment helps organizations strengthen their security posture and recognize potential risks to their compliance processes. It also evaluates the severity of the risk and minimizes its impact on business operations. In addition, risk assessment tools are procedures for assessing and managing risks in an organization. Therefore, it can be your first step in building an effective cybersecurity management system. The use of tools offers in-depth knowledge about cybersecurity and helps in the decision-making process.
This article delves into risk assessment tools and how they work to improve an organization’s security posture. Reading the article can help you better comprehend risk assessment in cybersecurity and the impact of risk assessment tools on your business.
WHAT IS A CYBER RISK ASSESSMENT TOOL?
A cyber risk assessment tool allows organizations to recognize potential risks, evaluate their impact, and create a mitigation strategy. Risk assessment tools help your business manage present risks and lower the chances of reoccurrences. Numerous tools include innovative predictive analysis features that give businesses information and prepare for possible future risks. In addition, the risk assessment tool assists you in creating a proactive, step-by-step plan that supports your current position and improves your security protocol. These tools help by finding security gaps, identifying persistent trends, and creating mitigation plans that make things safer. In this context, analyses and statistical methods examine the collected data and entice business conclusions.
Furthermore, these tools help you understand your organization’s exact cybersecurity posture. The primary objective of the tool is to determine the impact of potential threats on your assets. The tools help prioritize risk, mitigate, and quickly respond to new threats.
TOP 9 RISK ASSESSMENT TOOLS FOR BUSINESSES IN 2024
Risk assessment tools are used to compact your organization’s security measures. Thus, you must select an appropriate tool to integrate into your security infrastructures. Here, we discuss nine risk assessment tools that you can incorporate into your security process:
1. Automated Questionnaires: Questionnaires are essential to cybersecurity and determine your third-party associated risks. However, creating manual questionnaires and validating the responses can be daunting and resource-intensive. Therefore, using an automated questionnaire platform helps to address the challenges simply. These platforms allow the creation of vendor-specific questions that can be sent to many people within the stipulated period. Thus, it makes things transparent between the stakeholders and helps develop a mitigation strategy.
2. Security Ratings: It provides an unbiased, data-driven picture of your organization’s cybersecurity posture. The risk assessment tool was initially used to access third-party risks but is now used to monitor internal security initiatives related to an organization. In addition, it offers helpful information about many parts of security, such as managing attack surfaces and finding threats. Thus, companies can use security rating systems to check the answers to vendor questionnaires and maintain a holistic approach to vendor risk management.
3. Vendor-Provided Tools: Network solutions provider vendors can supply tools for scanning their products for issues. Thus, ensure that your vendor provides the tools as complementary services. For instance, Google offers several free security tools for checking the safety of systems linked to the network. Therefore, these can be used to determine your current risk profile with existing security assessment solutions.
4. Vulnerability Assessment Platforms: A vulnerability review aims to find holes in your IT system by listing and analyzing the existing security controls. The assessment report helps businesses better understand the danger of vulnerable spots on the network, allowing them to prioritize threats. In addition, applying an independent vulnerability assessment in your organization evaluates the vendor performance and creates business relationships with the vendors.
5. NIST Framework: The NIST Cybersecurity Framework offers companies a set of rules to lower cybersecurity risks. These rules are based on current standards and best practices. The NIST framework helps companies deal with cyber threats and makes it easier for internal and external stakeholders to discuss cyber risk management. Thus, NIST offers a uniform language for handling and managing cyber risks that are easily understood across the departments. The framework has five parts, each dealing with a different area of risk management. The information helps businesses ensure cybersecurity and aids in risk detection.
6. Penetration Testing: An objective of penetration testing is to find out how well the current security measures work while still meeting legal requirements such as PCI DSS, HIPAA, and SOC 2. It is an aggressive strategy that shows the real-world risks of collaboration and can help resolve the problem. Therefore, some examples of security testing are high-risk vulnerability testing, the magnitude of potential business impacts after an attack, and forensic analysis of post-security incidents.
7. Employee Assessments: Employees play a crucial role in cybersecurity practice. Proper employee training also lowers the risk of cyber threats. It reduces the risk of clicking on phishing emails, downloading malware, or giving the wrong permissions to access secure data. In addition, the training will inform them on how to respond during an attack. These risk assessment tools ensure your company has the best data breach response plan for mitigating emerging risks.
8. Third-Party Risk Assessments: Vendors and contractors have partial access to any organization’s network systems. Therefore, vendors are technically outsiders of the company but have routine access to your client’s network. The hackers are aware of this and can take advantage of it. Secure data access becomes superficial once the hackers manipulate the vendor’s system. Thus, the vulnerability assessment uncovers the potential risks in data access and security controls. The process ensures that the vendors have strong cybersecurity practices to prevent security risks.
9. FMEA: The Failure Mode and Effects Analysis (FMEA) is a risk assessment tool discovered in the 1940s. It is well-recognized that every process and result has some level of risk. FMEA is a robust risk assessment tool that helps businesses find and reduce these risks before occurrence. Therefore, FMEA can reduce the chances and effects of cybersecurity failure. In addition, the process improves market reputation and product performance. FMEA is a tool for constantly improving processes. Regular FMEA reviews to ensure that new risks are found and dealt with promptly. This continued dedication to risk management through FMEA helps businesses avoid problems, stay ahead of the competition, and build a reputation for providing trustworthy, high-quality products and services.
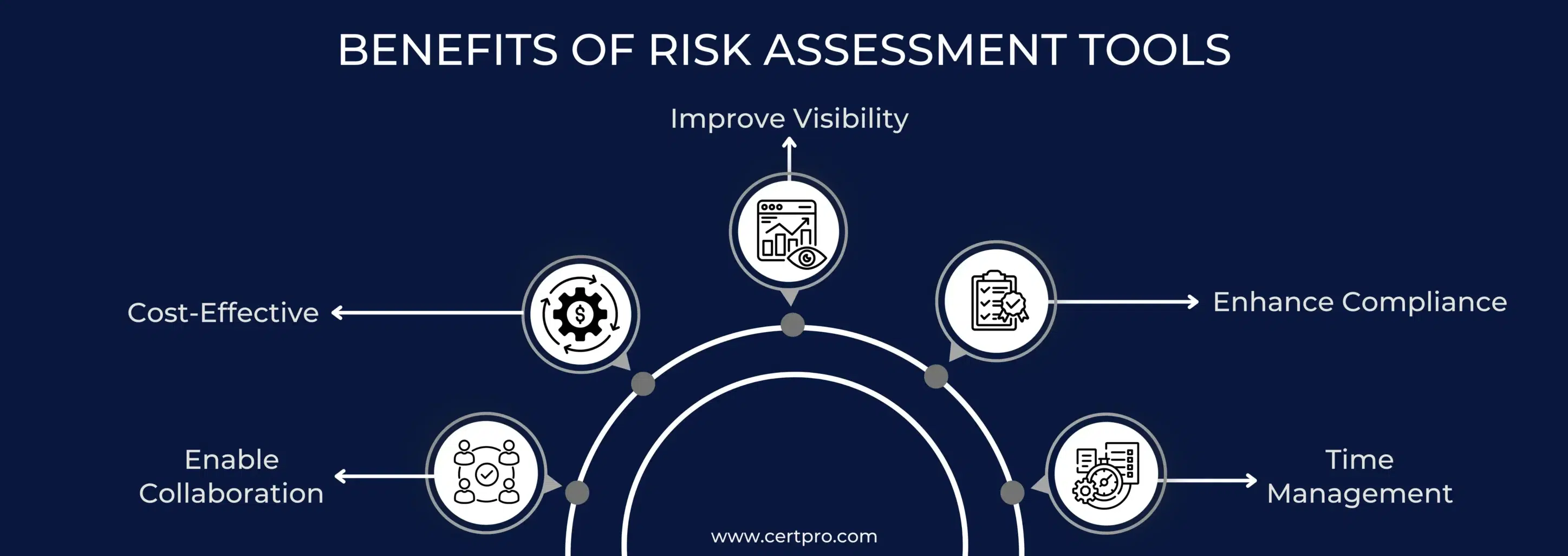
BENEFITS OF RISK ASSESSMENT TOOLS
Companies can benefit from using risk assessment tools to improve security protocols. The following are some of the advantages:
Improve Visibility: The risk assessment tools help users understand potential risks. The tools provide comprehensive data to evaluate the possible effects of potential threats, identify flaws, and prioritize threats according to severity. Thus, the overall aspects improve your organization’s visibility and help you make informed decisions.
Enhance Compliance: Risk assessment tools make the compliance process straightforward and find gaps in your functionality. Thus, businesses can get information about their vulnerabilities and create a plan to improve the standard. The tool prevents the risk of non-compliance and penalties.
Time Management: Businesses can save time and effort by conducting regular monitoring. Risk assessment tools streamline the operation process, allow users to track progress, and ensure compliance. Thus, it helps organizations identify emerging threats while reducing administrative loads.
Cost-Effective: Investing in risk assessment tools can reduce the financial burden by avoiding penalties and fines due to non-compliance. In addition, many risk assessment software offers flexible pricing for different business plans. Implementing a risk assessment tool simplifies the compliance process and streamlines the operational process.
Enable Collaboration: Executing a risk analysis tool fosters collaboration between the different teams within the organization. It creates coordination and cooperation in managing risk. In addition, it offers unified processes for sharing essential data across organizational boundaries, ensuring everyone is on the same page about understanding and reducing the different risks that come with operations.
HOW TO SELECT THE RISK ASSESSMENT SOFTWARE FOR YOUR ORGANIZATION?
The selection of the risk assessment tools depends on your organization’s security practices and objectives. However, we are mentioning some of the expected points which need consideration while you are choosing the tool:
Determine the Expectation: First, you should determine what your business needs from risk assessment tools. This will help you determine the features and functions of your desired software. For instance, if you are responsible for managing risks across multiple projects, you should use software that is efficient at managing projects.
Set a Budget: Going for the cheapest option is only sometimes wise. You can choose risk assessment tools based on your capabilities. In this regard, market research is essential in selecting risk assessment software. You can also follow similar industries and their risk assessment tools to understand the situation. In addition, implementing risk assessment software requires expenses related to technical support and updates.
Check for Integration: This is one of the main features of a risk assessment tool. It will determine its operational efficiency. In addition, the tool must be capable of working well with your existing infrastructure and providing you with a complete view of risks in your organization.
Request for Free Trial: Always ask for a free trial of your chosen risk assessment software before purchasing. This helps you understand the tool’s capabilities in managing risk in your organization. Thus, the free trial is essential for confirming the tool’s capabilities.
FINAL THOUGHTS
In the era of cybersecurity, your organization requires security measures to eliminate the risk of data breaches. As cyber threats become more complicated, it is essential to have access to tools for assessing cyber risk. Thus, an effective risk assessment tool ensures cybersecurity in your organization. You can find multiple risk assessment tools and software in the market. Various organizations are offering risk assessment software to improve security protocols. You are responsible for choosing an appropriate tool per your organization’s needs. Using tools has multiple positive impacts on your business growth and sustainability. Thus, think wisely and decide to consider your future goals.

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
FAQ
What is risk automation?
It is a process in which technology automates the manual processes of evaluating and organizing risk data to increase speed, ease of use, and accuracy.
What are automated risk assessment tools?
An automated risk assessment tool uses risk data to find any potential gaps. Tools like automated surveys, security ratings, penetration testing, threat data platforms, and security management systems are all part of this.
How often should I conduct a cybersecurity risk assessment?
The frequency of the review depends on the type of business and its risks. However, cybersecurity risk assessment can be performed at least once a year.
What is qualitative risk assessment?
A qualitative risk assessment or analysis involves finding possible risks or threats and determining their likelihood of occurring. Its primary purpose is to help people understand the likelihood and impact of various risks and identify areas needing extra security management attention.
What is quantitative risk assessment?
Quantitative risk assessment or analysis is a structured way to determine potential risks. This process depends on data to determine how risks will affect businesses.
INFOSEC RISK MANAGEMENT IN 2024: EFFECTIVE TIPS FOR SIMPLIFICATION AND MITIGATION
In today's businesses, the value of information is no less than any asset a company possesses. However, consecutive cyberattacks and threats disturb the collecting and storing process of information. Thus, the incident of emerging cyber threats enhances the risk to...
COMPLIANCE RISK MANAGEMENT: EXPERT STRATEGIES AND BEST PRACTICES
Compliance risk considers the organization's potential legal, material, and financial losses due to compliance failure. Thus, compliance risk is known as integrity risk. Organizations of all sizes are exposed to compliance risk. Hence, compliance failure results in...
TOP 7 DATA LOSS PREVENTION STRATEGIES IN 2024
In the contemporary business landscape, data is the cornerstone of organizational vitality. Businesses leverage data extensively to inform decisions, maintain competitiveness, and foster expansion. Nonetheless, they encounter multifaceted challenges emanating from...




