The world and businesses are changing together. Now, companies have transformed into online operations and transmitted data electronically. Therefore, cybersecurity become a key consideration for companies. Incidents of data breaches and data security are now familiar, but eliminating online data handling is still impossible in this digital era. Thus, companies are focusing on data security enhancement to sidestep the risks. In this regard, SOC 2 certification helps protect the data and maintain data integrity. Therefore, denying the importance of data security in this digital age is an unintelligent way to address the problems. Organizations are required to follow the correct steps to ensure data security. Like all other regulatory compliance, SOC 2 certification needs an audit to confirm adherence to the regulations.
Service Organization Controls (SOC) are a series of accounting standards set by the American Institute of CPAs (AICPA). The standard is widely recognized as financial and operational controls in service organizations. This blog will reveal the impact of SOC 2 certification on organizations and identify how it helps with customer retention and acquisition.
OVERVIEW OF SOC 2
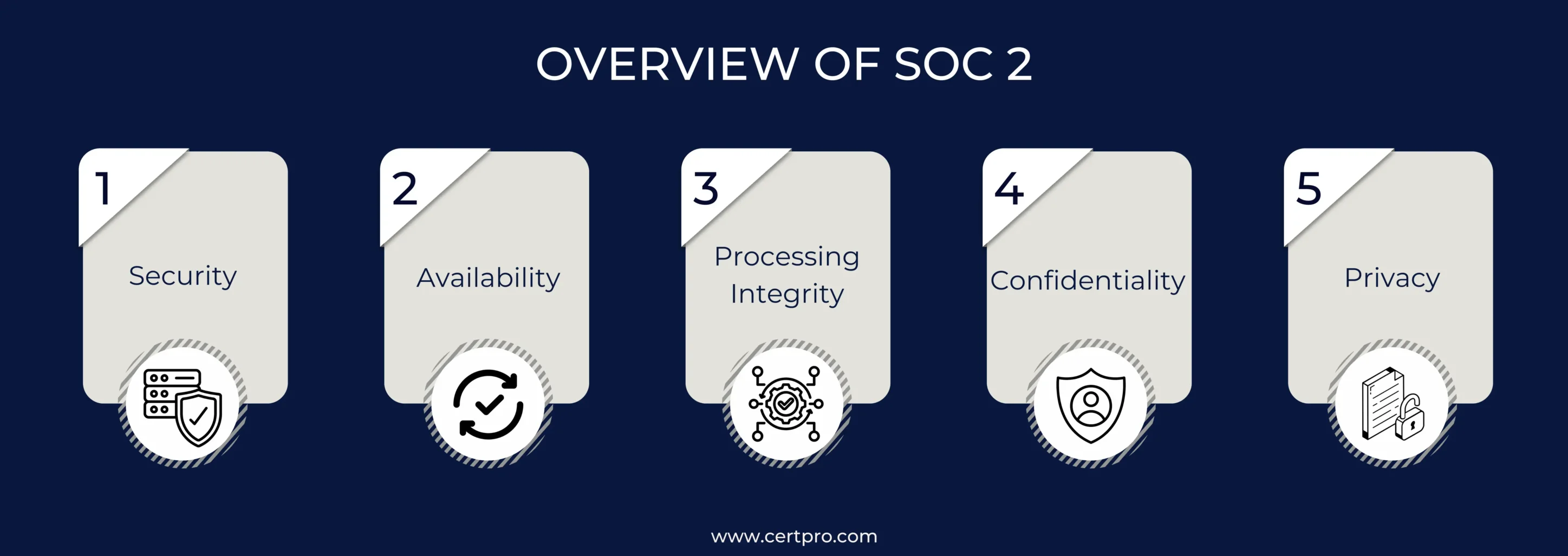
It is a framework for managing data security in your organization. The standard is appropriate for service providers who store customer data in a cloud setup. SOC 2 certification ensures the organization follows the trust service principles in managing its clients’ data. The standard offers comfort for service providers and their clients regarding safe data handling. By implementing SOC 2 compliance, your company can stay relaxed about data privacy and security. When discussing SOC 2, we should know about its five principles of trust. Here is the list:
Security: Security is an integral part of SOC 2 compliance because it keeps information safe from people who shouldn’t have access to it. In this context, your organization can implement firewalls, two-factor authentication, and intrusion deception systems for security. In the case of financial organizations, implementing advanced encryption strengthens security measures.
Availability: It is focused on the availability of the systems used to process and store data. The principle does not perform specific performance but makes the systems available as agreed upon with clients. Suppose a cloud storage guarantees 99.9% uptime, which shows that the company follows this concept.
Processing Integrity: It ensures that system processing is completed in a timely manner. Therefore, it is essential for organizations that process transactions or handle sensitive data. For example, e-commerce companies need this rule because they hold thousands of daily transactions. The integrity of the handling also ensures that the deals are done correctly and in a reasonable amount of time.
Confidentiality: The segment signified that some data are classified as confidential and shared in restricted conditions. For example, data from legal firms or financial sectors is considered sensitive. Thus, the data remains confidential and accessible with permission.
Privacy: It addresses the system’s use, retention, disclosure, and disposal of personal information under the law. Therefore, it is widely used in healthcare sectors where patient data must be managed strictly with privacy.
HOW DOES SOC 2 CERTIFICATION PROTECT BRAND REPUTATION?
Once you know what SOC 2 is and how it works with trust, you must learn more about how it can help protect your brand’s image. Digital tools make everything stand out in the world we live in. Because of this, data hacks can cost money and hurt your image. Therefore, getting SOC 2 certification is a smart way to protect your image and keep your finances in good shape. Let’s look at how SOC 2 helps the company and its reputation:
Improving Security Measures: Implementing compliance helps you maintain a robust framework against cyber threats. The certification process ensures risk assessment, offers employee training, and creates an incidental response. In brief, the compliance process requires internal and external auditing that strengthens the security process and reduces the chances of flaws.
Dodge the Impact of Data Breaches: SOC 2 certification prevents data breaches. In many cases, it was observed that SOC 2 compliance had identified and managed the threats before escalation. In addition, statistical data suggested that companies with SOC 2 compliance experienced fewer security incidents. Thus, SOC 2 compliance effectively influences your organization’s functioning.
Uplift Brand Reputation: Data breaches negatively impact a brand’s credibility and can lead to a loss of trust in the market. Customers can lose faith if the organization fails to protect their sensitive data. Hence, to avoid such consequences, organizations must implement SOC 2 compliance to create positive recognition in the market.
Testimonials from different businesses show how helpful SOC 2 is for managing reputations. For example, a tech business might say that its loyal customers are due to its strict adherence to SOC 2 standards.
WHY DOES SOC 2 CERTIFICATION OFFER COMPETITIVE BUSINESS ADVANTAGES?
Now, considering the impact of SOC 2 in holding the company’s reputation, let’s discuss how SOC 2 benefits your organization in the competitive market. Further, SOC 2 certification is more than compliance; and it helps you stand out from the competition. Let’s dig around the advantages:
Creating Trust: If you think SOC 2 compliance means following the checklist, you must correct it. It is a symbol of trust and dependency among customers and partners. Customers are now finding trustworthy companies to share their details. Regular news of data breaches makes them consider their data security and privacy. Therefore, companies that are SOC 2 compliant are the first choices due to their reliability and security. Why are trust and dependency on the customer’s end necessary for your business? Companies must create trust in the market and transform it into tangible business outcomes. Hence, companies prioritizing data security often find them in favorable conditions that help their customer retention and acquisition.
Improving Business Partnerships: SOC 2 compliance creates opportunities for new businesses and collaborations in industries where data security is a prime concern. In the B2B sector, it helps in collaboration as many organizations demand SOC 2 certification from their vendors. SOC 2 compliance shows possible partners that you care about data security. Therefore, a partnership with your business guarantees data security. Hence, the certification helps in the tech, healthcare, and banking sectors.
Enhancing Brand Values: Your organization’s commitment to data security significantly enhances brand values. Nowadays, customers are concerned about their data security. Thus, being a complaint can improve your brand values in the competitive market. It creates a substantial distinction in the market and secures customer loyalty for your organization. Accordingly, it positively influences your business growth and stability. Hence, to improve your brand reputation and acceptance, apply SOC 2 to enhance your organization’s credibility.
HOW DOES SOC 2 COMPLIANCE HELP IN CUSTOMER RETENTION AND ACQUISITION?
After discussing why SOC 2 is essential for standing out in competition, let’s focus on how it helps with customer retention and acquisition. Businesses require trust in the market to expand their opportunities. Similarly, SOC 2 certification ensures that customers’ data is safe and helps retain customers for a long time.
Attracting Potential Customers: Customers become security conscious and avoid the risks related to digital data. Therefore, customers often seek organizations with data security commitments that safeguard their sensitive information. Thus, SOC 2 compliance addresses these concerns and denotes your organization’s commitment.
Fostering Long-Term Relationships: Trust is the primary foundation of business. It helps in business development and growth in the competitive world. Customers who find your organization’s commitment to data security become confident that their data is safe. Thus, they become loyal customers for your brand, essential for sustainability.
Enabling Business Growth: The statistical evidence shows that businesses with solid security measures, like SOC 2, often improve customer retention and acquisition rates. Your organization’s commitment attracts potential customers and makes them loyal to your brand. Thus, it helps in business growth and expansion.
HOW DO YOU STREAMLINE YOUR OPERATIONS WITH SOC 2 AUDITS?
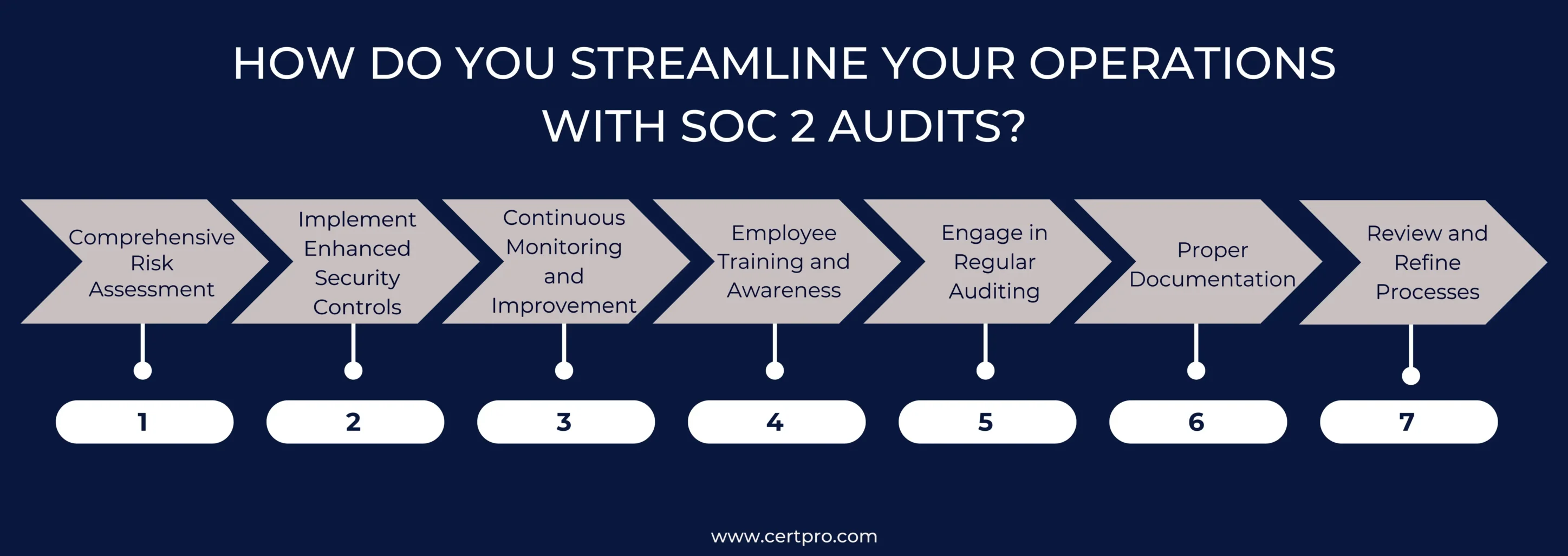
Knowing how SOC 2 certification helps your business run smoothly and builds customer trust is essential. Thus, you can improve operational efficiency, security, and business stability, which are vital to your business’s success. Let’s articulate some of the necessary steps in the process.
Comprehensive Risk Assessment: The first step is to examine your security methods closely. This review is crucial for finding vulnerabilities and ensuring compliance with SOC 2 standards. Knowing how effective your security measures are against SOC 2 standards helps create a well-thought-out action plan.
Implement Enhanced Security Controls: The next important step is to create robust security rules that meet SOC 2 standards. This signifies fixing the weaknesses that have been found. Consequently, better data encryption, access control systems, and intruder warning systems are some examples of better security controls.
Continuous Monitoring and Improvement: As soon as security measures are implemented, the focus changes to continuing oversight of the process. Therefore, close monitoring of security systems is necessary to promptly find any problems or breaches. You should keep changing based on the tracking results to ensure that security method controls are up-to-date and effective.
Employee Training and Awareness: Training and making employees aware of SOC 2 certification are essential for aligning things. Staff should be taught why data security is critical, the rules and policies, and what they can do to ensure compliance. Security should always be a priority; regular training can help create a culture of security knowledge.
Engage in Regular Auditing: Regular SOC 2 audits are needed to review how controls work and ensure ongoing compliance. The audit should be performed periodically, and experienced auditors should conduct it. The results of these audits are essential for finding ways to improve things and keeping operations running legally.
Proper Documentation: Keeping detailed records during the SOC 2 certification process is imperative. Thus, risk assessments, changes to security controls, findings, training workshops, and audit reports must be documented. The proper paperwork is necessary to show that you follow the rules during reports and internal reviews.
Review and Refine Processes: Finally, use the feedback from SOC 2 audits to improve your security processes. To ensure that your security measures keep up with new threats and changing business needs, you must keep reviewing and improving them based on what you learn from audits.
FINAL THOUGHTS
Therefore, understanding the basic ideas behind SOC 2 certification and SOC 2 benefits your business. We comprehend that SOC 2 compliance is about more than just meeting regulatory requirements. It is a strategic advantage that strengthens your security and protects your brand’s reputation. In addition, it gives you an edge in the market.SOC 2 compliance can help you gain customers’ trust and show that you care about protecting their data. Therefore, this trust becomes a valuable tool for attracting and retaining customers. SOC 2 compliance helps your company’s economic status by reducing functional costs and unnecessary expenses.
Now, consider the strategic advantage compliance can offer your global operations. Therefore, you can get guidance from CertPro on how to execute the SOC 2 compliance. Our expert advice and recommendations make the process simple for you. Additionally, we offer tailored services for our clients that minimize the cost of compliance. You can also visit CertPro.com for more detailed services. Reach out to us today and get comprehensive support from our experts.
FAQ
Is SOC 2 mandatory?
No, it is not mandatory. It is a regulatory requirement, not a legal requirement. Therefore, the implementation of SOC 2 ensures the security aspect of your organization and helps in business advancement.
What are the types of SOC 2?
SOC 2 compliance can be divided into Type 1 and Type 2. Type 1 evaluates whether the controls are set up correctly at a specific time, whereas Type 2 evaluates whether controls are designed and functioning as intended over a specified time.
How long does the SOC 2 report take?
The actual SOC 2 audit typically takes between five weeks and three months, depending on the scope of the audit and the number of controls involved.
What is the difference between SOC2 and ISO 27001?
SOC 2 primarily focuses on proving you’ve implemented security controls that protect customer data, whereas ISO 27001 asks you to prove you have an operational Information Security Management System (ISMS) to manage your security.
What is the difference between SOC 2 and SOC 1?
There is a significant difference between a SOC 1 report and a SOC 2 report. A SOC 1 report is mostly about financial controls, while a SOC 2 report is more about availability, security, processing accuracy, confidentiality, and privacy.

About the Author
Shivaprasad Shetty
Shivaprasad Shetty is an ISMS Lead Auditor and Consultant, adept at developing, implementing, and auditing ISO 27001-compliant frameworks. He is also well-versed in SOC 2 compliance, GDPR, HIPAA, and ISO 42001 standards. Shivaprasad excels in ensuring compliance across regulatory frameworks and fostering a secure organizational culture.
THE IMPORTANCE OF SOC 2 FOR SAAS COMPANIES: BENEFITS AND REQUIREMENTS
SOC 2 is a data security standard developed by the American Institute of Certified Public Accountants (AICPA). The standard offers the desired level of privacy and security regarding customer information. The rule is not mandatory, but it has multiple benefits for...
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...
SOC TOOLS: How They Impact On Security Aspect Of The Organization
The changing cybersecurity landscape increases the importance of Security Operations Center (SOC) tools. Hence, it is essential for strengthening digital defenses and protecting against cyberattacks. SOC tools help security teams detect, monitor, and prevent security...




