Securing sensitive information has become crucial in modern businesses. The increasing cost of data breaches in 2023 makes it more relevant and necessary. In addition, companies rely on technology and cloud services to continue their growth. Thus, securing sensitive data is now an evolved priority for companies. Hence, SOC 2 compliance has become a recognized standard in new tech industries to safeguard data. In the SOC 2 compliance process, the SOC 2 gap analysis is an essential step that helps to understand the compatibility of existing policies and procedures. The process helps develop remediation planning to protect businesses from data breaches. In addition, the SOC 2 gap assessment assists in implementing an effective strategy based on the organization’s goals. Thus, SOC 2 gap analysis is a fact-finding tool that reflects the current security posture against the industry-specific standard.
This blog will explain how SOC 2 helps organizations maintain their security posture. We will also discuss the gap analysis process and how to perform it to advance your organization.
HOW DOES SOC 2 HELP ORGANIZATIONS?
System and Organizations Controls provide a comprehensive framework for data security, privacy, and integrity. The compliance secures data for SaaS providers and assists in business growth. SOC 2 compliance denotes your organization’s commitment to cutting-edge data security standards. Thus, it supports the development of business relationships among customers and stakeholders. SOC 2 gap analysis uncovers your organization’s vulnerabilities in terms of security measures. A successful SOC 2 gap analysis ensures compliance requirements for the certification. SOC 2 compliance requires assessment and documentation of internal controls and procedures that are essential for compliance.
WHAT IS TSC (Trust Services Criteria)?
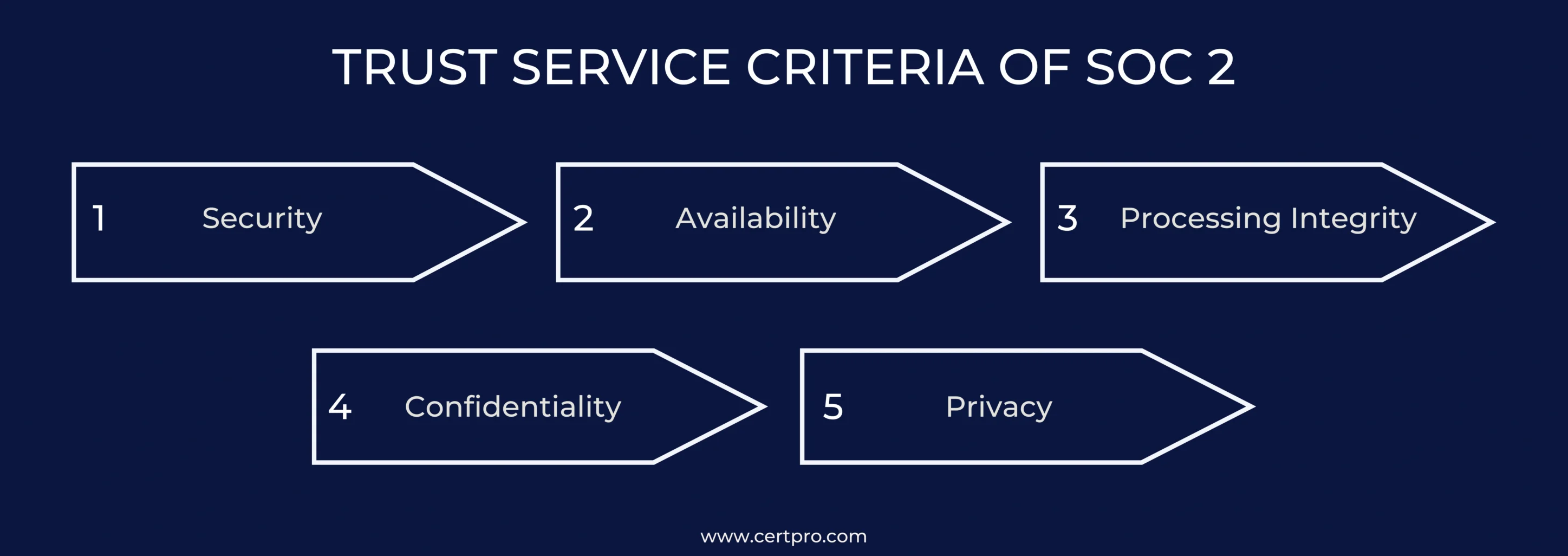
The SOC 2 compliance revolves around the five trust services criteria. Therefore, each TSC has a unique and distinctive measure for preventing the risk of data breaches.
Data Security: The criterion measures for data’s physical security include controlling the data centers and accessing logical and virtual data safeguards.
System Availability: It ensures the systems’ accessibility and prevents the risk of downtime. In cloud-based organizations, downtime can affect business continuity and slow the process.
Processing Integrity: This criterion ensures uniformity and consistency of data processing and confirms that the data processing systems are working accurately and timely.
Data Confidentiality: It protects the information designated as confidential from unauthorized access. The process considers the data relative to applicable rules and regulations.
User Privacy: The process ensures the privacy and confidentiality of specific personal information or sensitive data.
Thus, organizations lacking TSC adherence and implementation are recognized with a SOC 2 gap assessment. It is recommended that the organization undergo the readiness assessment before the SOC 2 final audit.
Related Links
SOC 2 in Australia
SOC 2 in Singapore
SOC 2 in Maldives
SOC 2 in Turkmenistan
SOC 2 in Philippines
SOC 2 in South Africa
SOC 2 in Mauritius
SOC 2 in Kenya
SOC 2 in Ethiopia
SOC 2 in Mozambique
SOC 2 in Nigeria
SOC 2 in Eqypt
SOC 2 in Oman
SOC 2 in Qatar
SOC 2 in Bahrain
SOC 2 in UAE
SOC 2 in Saudi Arabia
SOC 2 in Canada
SOC 2 in Europe
Wikipedia.com
HOW DO YOU DETECT A GAP ANALYSIS?
SOC 2 gap analysis may be carried out in several ways to find SOC 2 compliance deficiencies. Here are two such strategies:
1. Documentation and Self-Assessment: One strategy is to evaluate current documentation and self-assessment. These include the subsequent actions:
Examining Current Policies and Practices: Analyze the organization’s guidelines, practices, and safeguards for data availability, security, processing integrity, confidentiality, and privacy. Examine these procedures in light of the Trust Services Criteria (TSC) specifications.
Conducting Interviews and Surveys: Involve key stakeholders, including management, security teams, and IT staff, in interviews or surveys to learn more about current procedures and controls. Thus, this aids in locating potential holes or shortcomings.
Examining Incident and Audit Reports: Examine incident reports, internal audits, and any other pertinent paperwork to find any historical security incidents, weaknesses, or noncompliance issues. These reports might shed light on areas that need improvement.
Comparing Best Practices in the Industry: This evaluates the organization’s procedures compared to industry best practices and regulations, such as ISO 27001 or the NIST Cybersecurity Framework. Hence, it looks for discrepancies between the present methods and the required degree of compliance.
2. External Audit or Third-Party Assessment: Another option is hiring an external auditor or third-party assessor to evaluate thoroughly. These include the subsequent actions:
Selecting an External Auditor or Assessor: Pick an external auditor or third-party assessor with a solid reputation and knowledge of SOC 2 compliance.
Performing an On-Site Evaluation: The auditor or assessor visits the organization for a thorough review. To find areas where the TSC standards still need to be fully met, the auditor reviews the documentation, speaks with the staff, and examines the controls.
Gap Identification and Reporting: The external auditor notes their conclusions and identifies instances of noncompliance. Hence, a thorough report detailing particular flaws and weaknesses and suggestions for fixing them.
Remediation Planning and Implementation: Based on the external assessment report, the organization creates a remediation strategy to address the identified deficiencies. The plan also outlines specific steps, deadlines, accountable parties, and resource needs. Thus, the company implements the required steps to close the gaps and achieve SOC 2 compliance.
PERFORMING GAP ANALYSIS
A SOC 2 gap analysis is essential to the SOC 2 compliance process. It includes reviewing an organization’s current policies, controls, and processes to see where it needs to meet the Trust Services Criteria (TSC) standards. Let’s take a better look at how businesses can do a gap analysis well:
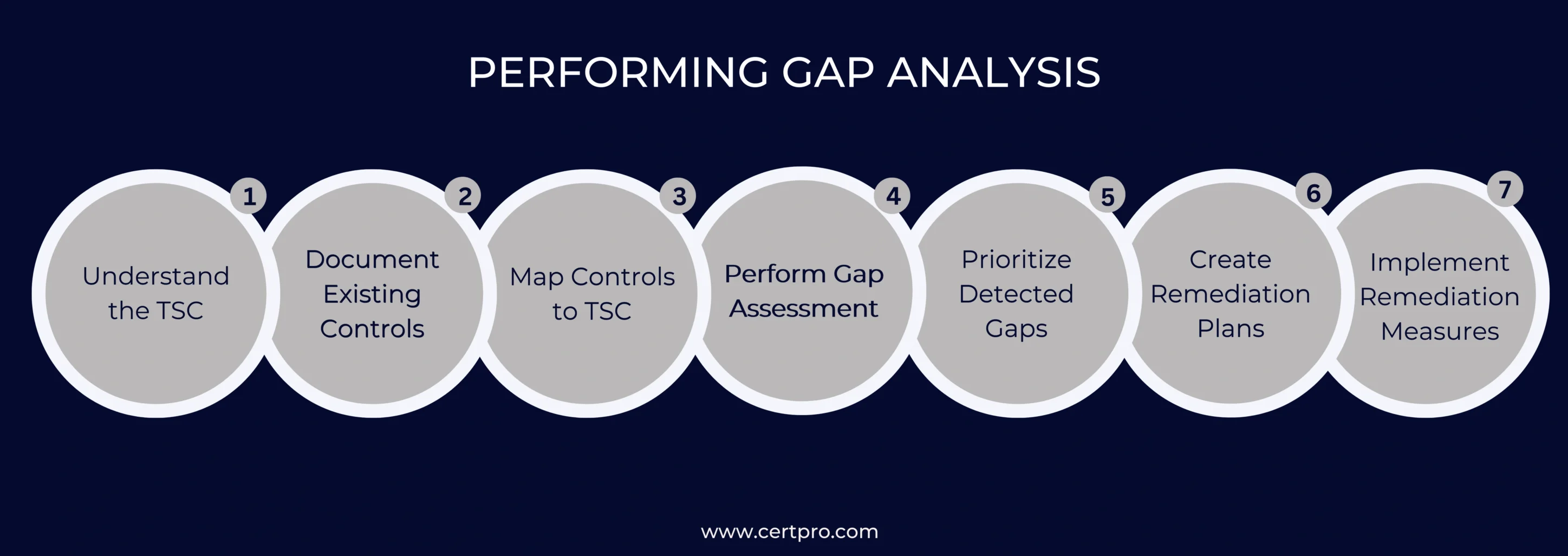
1. Understand the TSC: The first step in recognizing gaps is thoroughly understanding the TSC’s requirements. Hence, TSC includes security, availability, processing integrity, confidentiality, and privacy standards. Thus, familiarize yourself with each criterion to conduct a thorough evaluation.
2. Document Existing Controls: Outline the organization’s present data security controls, policies, and practices. This documentation thoroughly evaluates the current status and is a benchmark for comparison.
3. Map Controls to TSC: Align the described controls with the pertinent TSC criteria. This mapping process ensures that every control is assessed for the particular requirements it seeks to satisfy. It also aids in locating any possible holes or instances of non-compliance.
4. Perform Gap Assessment: As part of the SOC 2 gap analysis process, conduct a comprehensive study. Therefore, contrast the documented controls with the precise requirements to evaluate differences or deviations. These flaws include implementation errors, missing controls, or ineffective controls.
5. Prioritize Detected Gaps: After finding gaps, rank them based on their impact on security and compliance. Thus, it helps identify which gaps need immediate attention and correction.
6. Create Remediation Plans: Create a remediation plan outlining the procedures required to close the gap. The plan should include specific activities, deadlines, accountable parties, and needed resources.
7. Implement Remediation Measures: Implement the remediation plans considering the gaps found. This entails improving current controls, implementing new controls, or changing procedures to conform to TSC criteria.
Once the corrective steps have been implemented, regular monitoring is essential. Always check how well the control works in the legal setting; changes may need to be made. It helps companies understand the state of compliance and plan for achieving SOC 2 compliance. It allows companies to improve data protection, lower risks, and protect private data.
HOW DOES CERTPRO HELPS ORGANIZATIONS
CertPro offers cybersecurity services, regulatory compliance implementation, and continuous monitoring. We protect the sensitive data of our multiple clients through the implementation of SOC 2 compliance. Hence, our skilled professionals suggest a robust framework for security compliance. In addition, our knowledge and practical experiences assist in effective SOC 2 gap analysis, which is essential for the comprehensive framework. Hence, your collaboration with CertPro enables cost-effective services from our end with 24*7 support systems. Thus, we assist our clients in their compliance journey and help them maintain compliance.
Certpro believes in unique planning and execution to make the compliance journey easier. In addition, our practical SOC 2 gap analysis requirements find areas where your organization can improve and develop a plan. Thus, visit our site, CertPro.com, to learn more about SOC 2 compliance and gap analysis. You can also contact us if you have unique needs or need help. We’re here to help.
FAQ
How frequently should a company run a SOC 2 gap analysis?
The frequency of a SOC 2 gap analysis depends on a number of variables, including legal requirements and changes to the organization’s systems, processes, or controls. It is advised to perform a gap analysis on a regular basis, such as once a year or whenever substantial changes take place.
What is the SOC 2 Type 2 monitoring period?
The SOC 2 Type II report evaluates the performance of your internal controls over a certain time period, usually between three and twelve months. SOC 2 Type II audits require a bigger time and resource commitment.
Can businesses enhance their data security procedures with the help of a SOC 2 gap analysis?
Yes, by highlighting any weaknesses in the current controls and procedures, a SOC 2 gap analysis may assist firms in strengthening their data security procedures. It gives companies information on areas that need improvement and enables them to prioritize corrective actions to improve their overall security posture.
What must I search for while I examine a SOC 2 report?
The oversight of the service organization, vendor management programs, regulatory oversight, risk management procedures, and internal regulatory oversight are other items to look for in your SOC 2 report.
What is the expiration date for SOC 2?
The SOC 2 report’s normal 12-month validity period makes it easier to confirm that internal controls are installed and enforced appropriately over time. Customers will find it much easier to trust you with their private information as a result.

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
THE IMPORTANCE OF SOC 2 FOR SAAS COMPANIES: BENEFITS AND REQUIREMENTS
SOC 2 is a data security standard developed by the American Institute of Certified Public Accountants (AICPA). The standard offers the desired level of privacy and security regarding customer information. The rule is not mandatory, but it has multiple benefits for...
THE IMPACT OF SOC 2 CERTIFICATION ON CUSTOMER RETENTION AND ACQUISITION
The world and businesses are changing together. Now, companies have transformed into online operations and transmitted data electronically. Therefore, cybersecurity become a key consideration for companies. Incidents of data breaches and data security are now...
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...




