Data security is of paramount importance for companies, and one widely recognized standard that showcases their commitment to safeguarding data is SOC 2 accreditation. Businesses and their prospective customers, who want assurance about data security and customer data privacy protection against cyberthreats and malware, have driven the demand for SOC 2 compliance. Achieving SOC 2 compliance certification is no easy feat, as it entails a series of challenging tasks, including the SOC 2 audit and the selection of primary objectives. To gain a comprehensive understanding of SOC 2 and the steps involved in attaining it, this article provides detailed insights.
It’s worth noting that SOC 2 is not a certification in itself. Although commonly referred to as SOC 2 certification, the term is inaccurate. Rather, after successfully completing the SOC 2 process, qualified auditors provide “SOC 2 attestation” as evidence that a business has achieved SOC 2 compliance.
WHAT IS SOC 2?
The American Institute of Certified Public Accountants (AICPA) developed SOC 2, a cybersecurity compliance program. The initial purpose of SOC 2 is to know whether third party service providers store and process the data of customers in a secure manner.
SOC 2 is not a certification, as we all know, so what exactly is it? No matter how big or small the business is, any SaaS or technology services provider may adopt the SOC 2 framework. It supports businesses that keep customer data in the cloud, ensuring that these businesses continue to reduce the risks of data exposure. Its goal is to ensure that a company will uphold legal standards, protect the privacy and security of its customers’ personal information, and have risk-mitigation policies in place.
WHY IS SOC 2 REQUIRED?
This certification proves that your business has a system and set of protocols in place to minimize risks and offer the highest level of security for the data that has been stored in the cloud. Additionally, it demonstrates how particular your business is about the security of your customers’ data, which also contributes to a rise in client confidence.
Its major goal is to have improved security measures in place for the stored data. Depending on their particular needs, it enables businesses to implement the finest practices and procedures in the sector. In order to give consumers of these services validated reports of internal controls over such information systems, service companies are built to employ SOC 2. The reports address controls broken down into five categories known as Trust Service Criteria.
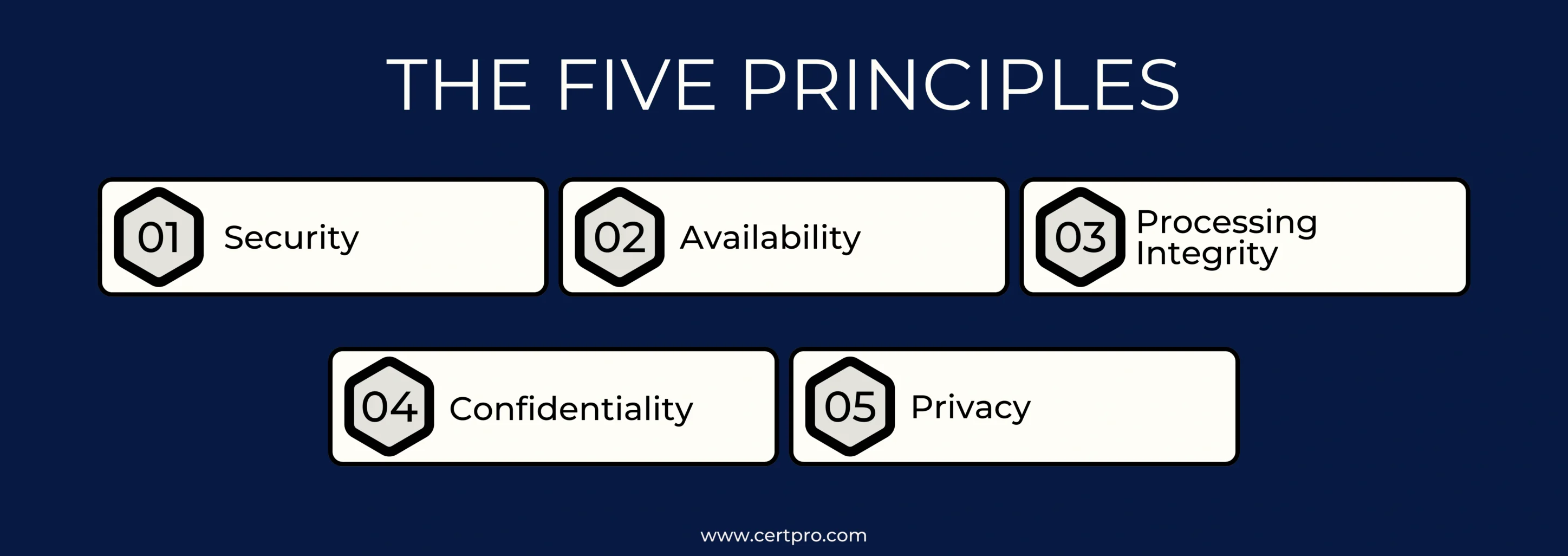
Five trust principles serve as the foundation for SOC 2 certification. It aids businesses in easily and methodically achieving SOC 2. The Trust Service Criteria (TSC) are five fundamental trust tenets. Let’s talk about these trust principles and how to use them to obtain SOC 2 certification.
TRUST SERVICE CRITERIA OF SOC 2
The five trust principles are:
- Security: The security concept focuses on avoiding unwanted access, preserving the confidentiality and integrity of data, and defending the organization’s physical and logical assets.
- Availability: The term availability demonstrates how essential it is to make sure that systems, services, and data are available and operating as intended with little downtime or disruption.
- Processing Integrity: This concept ensures that data is processed accurately and effectively throughout its duration by paying attention to accuracy, completeness, and timeliness in processing.
- Confidentiality: The confidentiality concept focuses on preventing illegal access to, disclosure of, or use of sensitive and confidential information.
- Privacy: In line with established privacy policies and any relevant privacy laws and regulations, personal information must be collected, used, retained, disclosed, and disposed of in accordance with the privacy concept.
These trust principles offer a framework for creating, putting into practice, and assessing controls that are in line with the goals of your company throughout this certification process.
When choosing the trust principles for auditing from the five listed above, Security should be added without hesitation for auditing reasons. We should include privacy in the audit if a company is in charge of processing and maintaining consumer personal information. Processing integrity must be taken into consideration while handling a customer’s financial information. If the business uses software as a service and keeps its data in the cloud, we should include availability. The majority of businesses, however, choose security reviews, privacy, accessibility, and secrecy. It is important to remember that we should only map and choose the TSC criteria that are required for our business. Not all requirements must be fulfilled.
HOW DO I ACHIEVE SOC 2?
After getting an idea of what the trust principles are, it should be easy to know what the main functions are needed in the journey to achieve this certification. Let’s go through the SOC 2 certification checklist.
Define the scope of your audit:
The first step to achieving not only SOC 2, but any certification purpose, is defining the scope of your audit.
This certification is used to demonstrate your organization’s dedication to security and raise client trust in your security program. Include all services and goods in the audit of business operations that customers are concerned about.
Smaller businesses often focus on the entire organization, while larger businesses with more expansive and diverse product lines should choose the areas they want to cover. However, if one part of the firm is functioning better than the others, your compliance program can run into problems. Now is the time to choose which TSCs to add and if the SOC will be Type 1 or Type 2.
Identify and conduct a gap analysis:
Analyze your cybersecurity program in relation to the SOC 2 controls once you have chosen the audit’s scope.
Before obtaining this certification, there are a number of administrative and technological security measures that are frequently ignored, and they may be trouble spots that need a lot of extra effort both before and during the audit process.
Document your cybersecurity program:
The auditor needs actual information to review in order to assess your security program. Simply informing the auditor that your users must utilize multi-factor authentication is insufficient. Who is obliged to have it must be specified in a policy, right? Which application categories are necessary to utilize it, and which ones are not? What authenticator applications are permitted?
A policy and proof that your business is adhering to the policy developed for them are required for the majority of controls. It takes a lot of work, but the end result will make your business much safer.
Selecting your auditor:
We are not going to lie. But this process is very strenuous. Not every auditor is equal. Since the AICPA administers the standard, practically any CPA may theoretically do a SOC 2 audit, but that doesn’t mean that every CPA should.
Your compliance process will endure if your auditors are bad. For a better job and a report of the highest caliber, it is very important to choose an auditor who is educated and has a better knowledge of SOC 2 and cybersecurity.
These factors are very important when choosing an auditor:
- Cost: It is essential that costs are covered in the budget you made for SOC 2 certification. And remember, the most important thing is that you will be paying for a SOC 2 type II audit each and every year.
- Experience of the auditor: Choosing an auditor is important; choosing an experienced auditor is crucial. Select an auditor with better experience and a higher rate of successful audits. Their practice should be specific to SOC 2.
- Timeliness: To ensure that everything runs smoothly and that important reporting or other benchmarks are finished on time, you need an auditor who can commit to a deadline.
CHALLENGES YOU FACE DURING SOC 2 ATTESTATION
1. Administrative controls are a nightmare for most companies. As they fail at performing the better version while they can’t match the SOC 2 requirements. It would be better to be careful with the administrative controls and learn more about them while undergoing SOC 2 certification.
2. For all of your important systems, you must check your access controls and permissions. Your Identity and Access Management (IAM) system, cloud services, networking devices, servers, VPNs, and other crucial items will all be included in this.
3. One more important aspect of the audit process is change control. Document every change that has been made in the company regarding software, configuration, and networking.
4. Mitigating the risk and managing vendors is the next part of this process that should be taken care of. They will be in every aspect and part of the SOC 2 certification, so you can’t escape them however you scope them.
Make sure that your providers, who are doing crucial tasks, don’t jeopardize your customers’ data upstream. You must inquire about your vendors’ security programs for the same reason that your clients are asking you for information about yours.
5. The control used to respond to specific cybersecurity incidents is known as incident response. These are the controls, which are essentially your response and recovery plan on how to handle unexpected threats and breaches. Problems that arise for most companies arise because they don’t have a plan to face these types of consequences. Even if they do have a plan, it might not be detailed enough to respond quickly to mitigate risks. Without a better backup plan, there would be chaos.
The best way to get rid of these types of risks is to have a step-by-step plan to face the event when it occurs. These steps should include preparation,damage control and analysis, management, and recovery to help you survive this kind of event.
WHAT HAPPENS AFTER GETTING SOC 2 CERTIFICATION
Congratulations! You reached here, and we know that it isn’t an easy task to achieve “SOC 2 Attestation”. It’s time to use your excellent report to expand your firm, assuming there are no exclusions.
When clients ask for your report from you, you’ll need to build up some form of mechanism for sending it to them. Requesters must sign an NDA before getting a copy of the SOC 2 report since it contains private information about a company’s security program.
Additionally, you must instruct your marketing group to begin mentioning your SOC 2 compliance certification status in your promotional materials! Any customer who is concerned about security will put you at the top of their list of potential vendors if you have a strong cybersecurity program.
HOW TO GET SOC 2 CERTIFICATION
To obtain SOC 2 certification, follow these 7 steps:
1. Choose Which Trust Principles You Would Like to Have Audited: Selecting Trust Service Criteria (TSCs) is essential for SOC 2 compliance. Security must be provided, privacy must be protected in order to manage personal data, and processing integrity is required while handling financial data. Because SaaS companies are cloud-based, Availability is frequently included. To ensure a customized approach, business processes must be aligned with pertinent TSCs. It’s crucial to acknowledge that not every trust concept holds true for everyone. This knowledge makes it easier to develop a sophisticated and practical SOC 2 compliance certification plan that is suited to particular business requirements.
2. Describe the Controls: Establishing controls in line with the Trust Service Criteria (TSC) that apply to your company is essential to attaining SOC 2 compliance. Administrative Controls and Technical Security Controls are two aspects to think about when streamlining this procedure.
3. Administrative Controls: Administrative controls include procedures for onboarding and offboarding team members, physical security, documentation policies, and effective people management.
4. Technical Security Controls: The goal of technical security controls is to protect your technical infrastructure from both internal and external threats so that client data is protected. Firewalls, access controls, multi-factor authentication (MFA), encryption techniques, and other systems are a few examples. Make use of online templates or seek advice from outside professionals.
5. Examine your security procedures as per trust principles: A best practice is an additional important but optional step in achieving SOC 2 compliance. Testing is essential after controls are put in place. Identify control gaps relating SOC 2 requirements, fix them, and undertake post-remediation tests to guarantee comprehensive compliance. This phase, known as the readiness assessment stage, examines if your business is prepared for external auditing after determining trust criteria and applying controls. For an objective assessment of your security posture, you can evaluate it yourself or hire an outside expert. Although this optional step comes with extra fees, it’s a commonly used security practice.
6. Have a certified CPA audit your SOC 2 certification report: The final stage entails hiring an outside auditor to evaluate your security systems and compliance posture. You will be asked to produce evidence relevant to various controls, procedures, and policies throughout this phase. Expect continued communication and engagement with the auditor, which will include the exchange of further evidence and insights into any temporary or consistent failures in control effectiveness. This participatory process may handle unanticipated issues. A normal audit lasts 4 to 6 weeks and includes extensive inspection and interaction between you and the external auditor.
7. Get a SOC 2 attestation report: Based on the performance of your policies and controls, the audit results decide whether the auditor delivers a qualified SOC 2 attestation report or a SOC 2 certificate. An unqualified report indicates conformity, but a negative report identifies problems in your processes. In the latter situation, resolving highlighted faults and undergoing another audit is recommended in order to receive a non-conformity-free report. This continuous approach guarantees that the SOC 2 certification is resilient and reflects effective rules and controls.
WHAT IS A SOC 2 TYPE 2 CERTIFICATION?
SOC 2 Type 2 certification, a widely adopted compliance standard, ensures robust security for third-party client data storage and processing. Issued by the AICPA, this certification involves a rigorous third-party audit, evaluating information security practices and procedures over a 6 to 12-month period.
The comprehensive examination covers Infrastructure, Processes, Data security, and Data handling. Obtaining the SOC 2 Type 2 attestation is valuable for client assurance and showcasing strong security practices to the broader audience. Despite the seeming simplicity, the certification process is intricate, emphasizing the commitment to stringent security standards in safeguarding sensitive client information.
FAQ
How long does SOC 2 certification take?
Developing a comprehensive security report akin to a SOC 2 Report typically involves a time commitment ranging from six months to a year for most businesses. These reports often require a minimum of six months and frequently extend to a full year or even longer. On the other hand, the production of these Type I Reports can be completed within a timeframe of up to six months.
How many controls are there in SOC 2?
An information safety management system (ISMS) must meet certain criteria in order to be established, implemented, maintained, and improved, according to ISO 27001. The bulk of its 114 controls, distributed across 14 categories, correspond to the Trust Services Criteria.
Can a SOC 2 audit have failed?
You cannot fail to qualify for this audit. It is the responsibility of your auditor to express views about your company in the audit’s final report. A “qualified” opinion might result from improperly planned or ineffectively functioning controls in the report.
How frequently are SOC 2 audits conducted?
A SOC 2 audit report is valid for 12 months from the report’s release date. To maintain ongoing compliance and strong security, organizations should undergo certification every year.
How to get soc 2 certification and How frequently should a business get a SOC 2 audit?
To obtain SOC 2 certification, implement controls aligned with Trust Service Criteria, engage an external auditor, and address any issues identified. Audit frequency varies based on business changes, regulations, and risk assessment.

About the Author
RAGHURAM S
Raghuram S, Regional Manager in the United Kingdom, is a technical consulting expert with a focus on compliance and auditing. His profound understanding of technical landscapes contributes to innovative solutions that meet international standards.
THE IMPORTANCE OF SOC 2 FOR SAAS COMPANIES: BENEFITS AND REQUIREMENTS
SOC 2 is a data security standard developed by the American Institute of Certified Public Accountants (AICPA). The standard offers the desired level of privacy and security regarding customer information. The rule is not mandatory, but it has multiple benefits for...
THE IMPACT OF SOC 2 CERTIFICATION ON CUSTOMER RETENTION AND ACQUISITION
The world and businesses are changing together. Now, companies have transformed into online operations and transmitted data electronically. Therefore, cybersecurity become a key consideration for companies. Incidents of data breaches and data security are now...
HOW CAN STARTUPS ATTAIN SOC 2 COMPLIANCE IN 2024?
Trust is crucial for startups to do well in today's digital world. It's vital for establishing credibility with clients, especially in a data-driven environment where privacy is the main component. Therefore, getting a SOC 2 compliance report is crucial to building...




