In today’s interconnected business landscape, third-party vendors play an important role in accelerating growth and improving operational efficiency for enterprises across industries. However, increasing reliance on external partners entails an increased level of risk, including regulatory compliance, data security breaches, financial instability, and brand damage. Protecting against these risks requires a planned and thorough approach to vendor management.
Vendor management refers to the oversight and regulation of transactions between a firm and its external vendors. It entails putting in place strong systems and solutions to reduce the risks connected with these collaborations. Vendor Risk Management (VRM) constitutes a vital component of vendor management, centered on identifying, evaluating, and mitigating risks associated with third-party providers.
In this blog article, we will discuss the necessity of reducing third-party risk through efficient vendor management techniques. We’ll look at the important components of vendor risk control, such as strategic vendor prioritization, stringent access control measures, ongoing monitoring and evaluation, automation adoption, insurance coverage review, and contingency planning. We’ll also go over the vendor risk management lifecycle, which includes stages such as onboarding, ongoing management, and offboarding and provides a methodical framework for managing vendor operations.
WHAT IS A THIRD-PARTY VENDOR MANAGEMENT?
Third-party vendor management is the control and regulation of transactions between a firm and its external vendors. Many organizations rely significantly on these providers to accelerate product introductions and keep operations running. However, such alliances expose businesses to a variety of risks, including regulatory compliance, brand damage, data security breaches, and financial instability.
Vendor access to a company’s network is a critical cybersecurity vulnerability that could compromise valuable corporate, employee, and customer data. To effectively mitigate these risks, businesses must implement strong vendor management processes and use Vendor Risk Management (VRM) solutions.
A complete vendor risk control strategy includes outlining the expectations, access permissions, and regulatory compliance criteria agreed upon by the organization and its third-party contractors. This strategy should include procedures for testing and assurance to validate the vendor’s ability to meet its responsibilities securely. Furthermore, it should include a detailed checklist defining the necessary measures for vendors to maintain an appropriate degree of risk mitigation. Businesses that follow these steps can protect their operations and strengthen their resilience against potential dangers from third-party activities.
WHAT ARE THE VENDOR RISK MANAGEMENT BEST PRACTICES?
Vendor risk management best practices include the following:
- Strategic Prioritization of Vendors: Every vendor poses a unique level of risk, demanding a systematic approach to successfully prioritizing them. Vendors can be classified as high, medium, or low risk by developing a risk rating system, such as weighing the chance and severity of a prospective data breach against associated expenses. This ensures that resources are spent appropriately, with a focus on minimizing the most severe risks.
- Strict Access Control: While protecting against unauthorized access is critical, failing to implement effective access control measures can expose organizations to risk. Recent investigations have revealed disturbing numbers, demonstrating a lack of complete third-party access lists and inadequate identification of parties with sensitive data access. Implementing Identity and Access Management (IAM) and adopting a zero-trust framework can help limit vendor access, reducing the likelihood of breaches caused by excessive permissions.
- Continuous Monitoring and Evaluation: Traditional risk management approaches are frequently ineffective, providing just snapshots of security postures. Accept security ratings as continual, quantifiable insights into vendor security, similar to credit ratings. These real-time assessments provide a proactive approach to risk management, allowing for continuous examination throughout your vendor portfolio.
- Adopt Automation: Implementing automation in vendor management operations can result in significant efficiency gains. Automate data gathering, risk assessment, compliance checks, and vendor onboarding to improve operational efficiency, consistency, and error reduction. This innovative approach to risk management optimizes resource allocation while increasing overall effectiveness.
- Evaluate Insurance Coverage: Verifying proper insurance coverage among third-party providers is critical for minimizing potential liabilities. Examine contractual agreements to ensure compliance with required insurance levels, protecting against unanticipated events. Regular appraisal of insurance needs, taking into account technology improvements and operational changes, helps to limit the risks associated with inadequate coverage.
- Prepare for adverse situations: Contingency planning is critical in the event of vendor noncompliance or unforeseen disruptions. Prioritize business continuity, disaster recovery, and incident response planning to reduce disruptions and prevent vendor failures. Proactive actions reduce consumer impact and ensure operational resilience in the face of third-party incidents.

VENDOR RISK MANAGEMENT PROCESS
Developing a thorough vendor risk management process is crucial, especially when promoting improved teamwork between different departments in your company. You will continue to undertake ongoing vendor security risk management with each new vendor you bring into your supply chain. Although companies may have different procedures in place, the general concepts are always the same.
1. Evaluation: Creating a vendor inventory, which entails identifying each vendor and their relationship to your company, is the first step in the study. After completing this phase, the business can go on to assess vendor risk in order to ascertain the extent of due diligence necessary and the inherent risk connected with each vendor relationship. The business can then evaluate the security posture of the third party and carry out a gap analysis.
2. Engagement: The company and the third party collaborate to address and resolve any identified deficiencies. This may entail establishing a security architecture specific to your sector. For example, healthcare firms must follow HIPAA laws, whereas vendors interacting with European clients must follow GDPR standards. When building your third-party risk assessment, make sure it includes industry-specific compliance and regulatory standards, with the goal of improving your business relationship with prospective vendors.
3. Remediation: The third party closes the cyberholes. This may entail implementing various security controls such as multi-factor authentication, limiting privileged access to data to only those who require it, and data encryption. It may also entail distributing security questionnaires to determine the vendor’s current compliance rules and procedures. Furthermore, companies should verify that the vendor contract includes stipulations relating to data protection and compliance with their organization’s vendor risk management policies, as well as reasons for vendor relationship termination and secure offboarding.
4. Acceptance: The company authorizes or rejects the vendor relationship based on risk tolerance, adherence to industry laws, and the service provider’s importance to the organization’s business operations. Approved vendors are documented, along with the reasons for approval. Similarly, if a vendor is rejected, the decision is noted, along with the reasons for the rejection.
5. Continuous Observation: Organizations must regularly monitor third-party vendors throughout the vendor management lifecycle to discover cybersecurity weaknesses. This proactive strategy is critical for dealing with emerging threats successfully. It also applies to the offboarding process, ensuring that any sensitive data provided by the vendor is no longer accessible and properly destroyed.
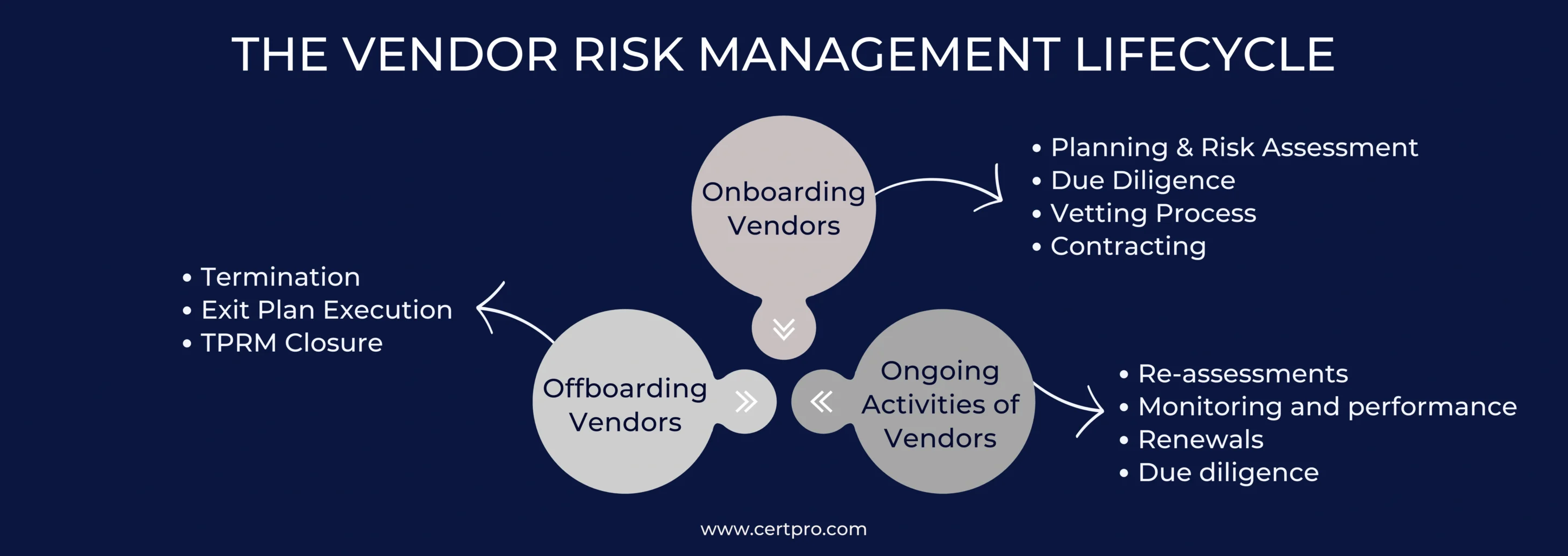
THE VENDOR RISK MANAGEMENT LIFECYCLE
The vendor risk management lifecycle, also known as the third-party risk management lifecycle, provides a systematic framework that includes three major stages: onboarding, ongoing management, and offboarding. This methodical approach makes it easier to handle vendor-related operations while also assuring effective oversight throughout the partnership. Beginning with the onboarding phase, which includes initial vendor assessment and integration, then continuous monitoring and evaluation during the ongoing management phase, and finally the offboarding phase, in which vendors are transitioned out of the system with proper risk mitigation measures in place,
There are three main stages in the vendor risk management lifecycle:
1. Onboarding Vendors: While it may seem tempting to expedite the onboarding process, particularly in urgent situations, it’s crucial to approach vendor onboarding diligently. The process involves several key steps:
- Planning & Risk Assessment: Begin by determining if the vendor’s product or service aligns with your program’s scope and designating responsibility for the relationship. Conduct a risk assessment to gauge the vendor’s criticality and inherent risks. Criticality refers to a vendor’s impact on your operations, while inherent risk exists naturally within their offering.
- Due Diligence: This step confirms the vendor’s legitimacy and controls. Gather and validate information, seeking expert opinions to assess sufficiency. Calculate the residual risk to determine acceptability.
- Vetting Process: Thoroughly review the vendor’s financial history, address consumer complaints, and conduct OFAC checks to avoid sanctions.
- Contracting: Finalize the vendor selection with a contract covering planning, negotiation, and management. Specify service level agreements (SLAs) and essential controls. Remember, the contract’s role extends beyond onboarding, impacting contract renewals and terminations.
2. Ongoing Activities of Vendors: Vendor risk and performance can fluctuate over time, emphasizing the need for continuous monitoring activities. These include periodic reassessments, ongoing risk and performance monitoring, formal performance management, contract renewals, and periodic due diligence.
- Re-assessments: Re-assessments involve reviewing and updating inherent risk assessments, with documentation collection for any changes at least annually for critical vendors.
- Monitoring and performance: Monitoring and performance activities entail regular assessments of vendors’ risk and performance between formal reassessments. Establishing a monitoring schedule based on inherent risk, tracking SLAs, and reporting vendor risk to senior management and the board are vital practices.
- Renewals: Renewals necessitate staying informed about contract expiration and notice periods to make necessary adjustments promptly.
- Due diligence: Due diligence ensures all documents, such as insurance certificates and disaster recovery plans, are current and accurate to mitigate risks effectively. Regular review and collection of updated documents are essential for maintaining compliance and preparedness.
3. Offboarding Vendors: The final phase of the vendor risk management lifecycle is offboarding or terminating the contract. This can occur proactively due to contract expiration or reactively because of performance issues or unmet SLAs. Regardless of the reason, having a documented termination process ensures a smooth transition.
Key activities in this stage include:
- Termination: Officially notifying the vendor that the contract won’t be renewed, typically following the contractual date.
- Exit Plan Execution: Implementing the exit plan developed during onboarding, which outlines the strategy for replacing the vendor, bringing activities in-house, or ending the product/service. Testing the plan’s viability and detailing roles, responsibilities, and tasks ensure a safe exit, including data handling and system access removal.
- TPRM Closure: Completing final steps like settling invoices, updating vendor status in systems, and archiving relevant material.
While outsourcing offers advantages, a robust vendor risk control program is crucial for protection. Understanding the three stages of the vendor risk control lifecycle is fundamental for managing risk effectively across vendor relationships.
FAQ
What is the risk matrix for vendor management?
The risk matrix aids in assessing hazards according to their likelihood and implications. Once you determine the risk level through this evaluation, you can then decide on the best course of action. Risks categorized as negligible typically do not necessitate an immediate response.
How does vendor risk differ from third-party risk?
While Vendor Risk Management (VRM) focuses primarily on vendors, Third-Party Risk Management (TPRM) assesses all third-party organizations. Many organizations work with several third parties on diverse tasks and roles.
Who is responsible for vendor risk management?
Vendor risk management falls under the responsibility of senior management and the Board of Directors. Every individual engaged in vendor interactions plays a significant role in maintaining smooth operations.
What are the goals of third-party risk management?
The goal of third-party risk management is to evaluate third-party interactions and their implications for the organization. Typically, this assessment organizes these tasks based on their risk levels, allowing the firm to optimize supplier risk management efforts for increased efficiency.
How can small businesses implement vendor risk management practices with limited resources?
Small businesses can implement vendor risk management best practices by prioritizing vendors based on criticality, focusing on key risk areas, leveraging affordable technology solutions for automation, collaborating with industry peers for insights, and seeking guidance from regulatory bodies or industry associations.

About the Author
NICOLENE KRUGER
Nicolene Kruger, Regional Manager in South Africa, is an experienced Legal Counsel with expertise in compliance and auditing. Her strategic, solution-driven approach aligns legal standards with business objectives, ensuring seamless adherence to regulations.
INFOSEC RISK MANAGEMENT IN 2024: EFFECTIVE TIPS FOR SIMPLIFICATION AND MITIGATION
In today's businesses, the value of information is no less than any asset a company possesses. However, consecutive cyberattacks and threats disturb the collecting and storing process of information. Thus, the incident of emerging cyber threats enhances the risk to...
TOP 9 RISK ASSESSMENT TOOLS FOR BUSINESSES IN 2024
Risk assessment helps organizations strengthen their security posture and recognize potential risks to their compliance processes. It also evaluates the severity of the risk and minimizes its impact on business operations. In addition, risk assessment tools are...
COMPLIANCE RISK MANAGEMENT: EXPERT STRATEGIES AND BEST PRACTICES
Compliance risk considers the organization's potential legal, material, and financial losses due to compliance failure. Thus, compliance risk is known as integrity risk. Organizations of all sizes are exposed to compliance risk. Hence, compliance failure results in...




