In recent years, data breaches have become headlines in many large companies. Technological advancements have made the hacking process more strategic and complicated. Therefore, organizations must consider the cybersecurity audit seriously to avoid breaches and have a firm grip over their cybersecurity program. Thus, you must implement a cybersecurity audit to understand the cybersecurity program’s insight and ensure the control implementation to improve the security posture. The security audit process can be daunting, but the organization can achieve excellent results in identifying cyber threats with the correct measures and approaches.
This article will explain the effective way of conducting cybersecurity audits, which can help organizations secure their data and reduce the risk of data breaches. Read the article to learn more about the security audit and its processes.
UNDERSTANDING CYBERSECURITY AUDIT
A cybersecurity audit is a comprehensive analysis and review of your organization’s IT infrastructure. The audit process helps to recognize threats and vulnerabilities in your organization. In brief, the security audit helps in:
- Identifying the risks and vulnerabilities of your organization.
- Improving the overall security posture.
- Ensuring compliance with regulatory standards.
- Improving the incident response system.
- Protecting sensitive data from hackers and ensuring customer trust.
- Ensuring proactive threat detection and prevention of risks.
As technology and digitalization grow, they bring new threats to businesses. Because of this, the security review process needs to find these threats and take steps to stop them. There will be more risks if your company doesn’t have an audit plan. Your business could have problems with not following the rules, which could have legal and financial effects. On the other hand, non-compliance means that your company doesn’t follow the standards that are specific to your business. So, if your company is not following the rules, it makes data breaches more likely. Ultimately, your company will be responsible for mishandling private data and must pay hefty fines. When companies get regular cybersecurity checks, they protect themselves well enough against some risks. It also lets the security team set priorities for fixing risks based on how bad they are.
REASONS FOR CONDUCTING A CYBERSECURITY AUDIT
A cybersecurity audit’s primary goal is to make sure the company is up to code. The audit process determines how well your company follows safety practices and industry-specific rules. As a result, the audit method helps find gaps and add new controls to close them. There are several reasons why a business should do regular safety checks, such as:
- Monitoring your organization’s infrastructure, systems and controls to identify potential threats.
- The audit ensures that the process meets the compliance requirements and mitigates the potential threats.
- Finding out how well and how efficiently cybersecurity operating systems and processes work.
- Checking the computer systems, security measures and management methods set up to lower risk.
- Creating backup plans to protect against hacking or other emergencies.
Some of the most important parts of any cybersecurity audit are reviewing the company’s cybersecurity policies, creating an all-encompassing approach to cybersecurity, testing workers’ cyber skills and helping the company begin risk-based auditing projects.
FREQUENCY OF AUDITS TO ENSURE CYBERSECURITY
How often you should do a cybersecurity audit depends on several things, such as the type of business you run, the size of your company, the level of risk, and any laws or rules your industry has. You should do regular cybersecurity checks to ensure that your systems and files are always safe. Keep these things in mind as you decide how often to check for cybersecurity:
Annual Audits: The first thing that most companies should do is a full cybersecurity audit at least once a year. This way, you can evaluate your protection, find weak spots, and make the necessary changes.
Regular Audits: Regular vulnerability reviews and audits once a year are vital to finding and fixing security holes. Depending on their size and complexity, some organizations often conduct these evaluations every six months, every two years or more.
Audit after Significant Changes: Organizations need cybersecurity audits whenever their IT systems change. Thus, changes like network merges and new technologies are all part of this. It is essential to ensure that security measures are still in place and work well with the new setting after these changes.
Regulatory Requirements: Suppose your organization follows specific cybersecurity regulations. These regulations mandate that you conduct a security audit within a particular period. Therefore, the process finds flaws in the practice and rectifies them to continue the compliance journey.
Incident Response Audit: Conducting an audit after a security breach or other incident is essential to your company’s incident response method. This will help you determine what went wrong and how to improve your security so that it doesn’t happen again.
THE SCOPE OF A CYBERSECURITY AUDIT
The audit ensures an in-depth analysis of your organization’s security posture. Its primary objective is to identify your organization’s vulnerabilities and potential threats. In addition, some other scopes of cybersecurity audit are listed below:
- The audit helps review network access control, data encryption, and data transmission processes.
- Further, the process reviews your organization’s network, security, anti-virus configurations, and security monitoring process.
- It allows the organization to review its role-based access controls and multi-factor authentication.
In addition, a cybersecurity audit may also look at cyber risk management, cyber risk governance, legal, regulatory, contractual requirements, technical security controls, business continuity, and incident management.
TYPES OF CYBERSECURITY AUDITS
Auditors outside the company or the internal audit process can do the audit. It is experienced professionals with a lot of information from specialized companies who do external cybersecurity audits. These experts know a lot about security measures and use the most up-to-date software and tools to do an audit. Professionals can find holes and mistakes in how your business handles digital risks. Employees of your company do internal security checks. Because of this, it can be done more often and is more practical because you can see the tools and methods used internally. Regarding security, internal auditors know what the business needs and can make the report fit those needs.
There are clear benefits and goals for both external and internal security audits:
External Security Audit:
- Since external auditors are not involved in the company’s day-to-day processes,hence they can give a fair opinion.
- External auditors often know how to conduct security audits in a complex business setup, and their experience can help in the process.
- External auditors examine the company’s security policies without bias or conflicts of interest from within the company.
You need to find the right and affordable auditing company to get the most out of the external security audit. In this context, CertPro can be the best option for your external audit. Share the correct and relevant information with us, and we will find any gaps in your process.
Internal Security Audit:
- An internal audit is best, as the employees know more about the company’s internal systems, methods, and culture, allowing the auditors to do a more thorough evaluation.
- There may be a lower cost to performing internal audits because the organizations do not require outside assistance.
- You can perform internal checks regularly to monitor and evaluate your organization’s security measures.
- When a company does an internal audit, it can focus on its special security issues and needs.
Even though external audits can be more helpful, many businesses still choose internal audits because the process is cost-effective and convenient.
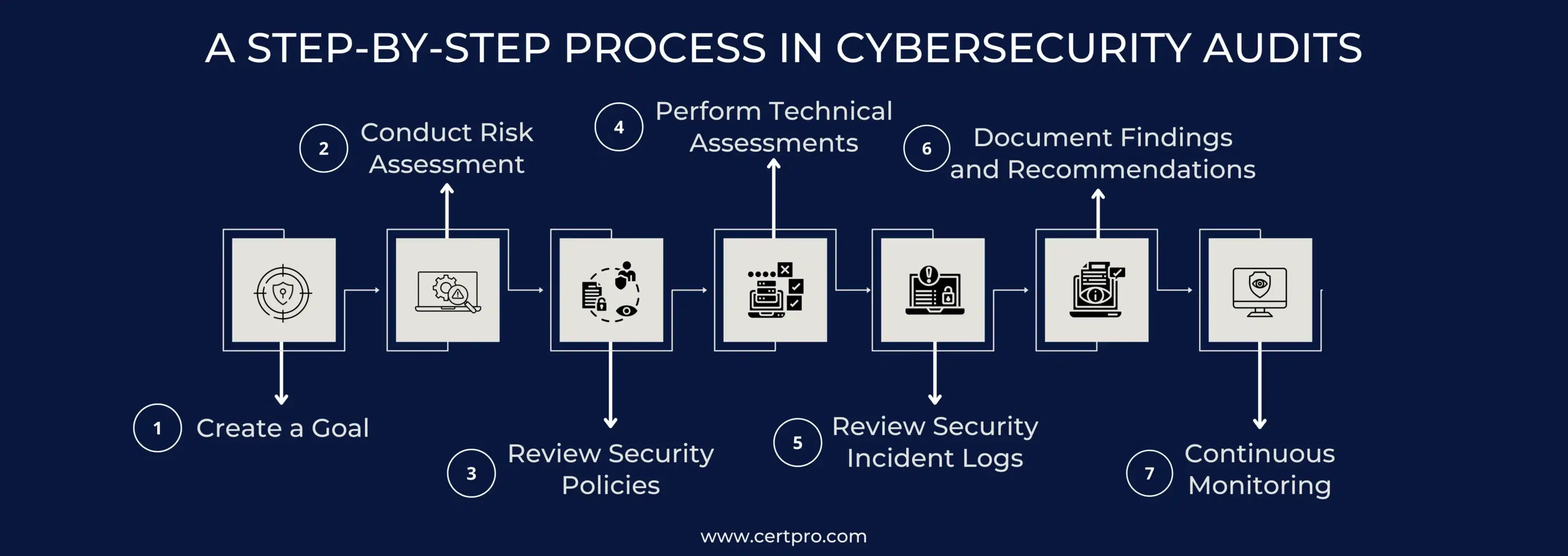
A STEP-BY-STEP PROCESS IN CYBERSECURITY AUDITS
It is vital to follow best practices when performing a cybersecurity audit. Here are some steps that help you understand auditing in cybersecurity.
Create a Goal: Clearly understand your cybersecurity audit’s aims and targets. This will help the auditors focus on their work and look closely at all the critical areas of concern. Such cybersecurity audit examples will enable the auditor to focus on a particular aspect. Suppose an organization is performing an audit to evaluate its security controls. Therefore, the auditors must conduct and review the controls as needed. Some organizations will concentrate on finding the potential vulnerability in their process and response plan. The audit process must be performed based on the objectives.
Conduct Risk Assessment: You should perform a risk assessment to find threats, weaknesses and risks unique to your company. In general, companies are looking at the importance and worth of data, the results of possible breaches, and the likelihood of various types of cyberattacks. If you know the risks, you can decide which areas need more attention during an audit and give extra resources to those areas.
Review Security Policies: The audit process will review the company’s current security rules, policies and processes. Consequently, it ensures that the controls and practices are aligned with industry-specific practices. The audit process assesses the effectiveness of access authentication, data encryption and data provision process. Further, the process reviews the employee’s training process and documents incident response for future strategies.
Perform Technical Assessments: Cybersecurity audits conduct technical assessments of the company’s IT system to find holes and weak spots. This could include scanning for vulnerabilities, conducting penetration tests and reviewing the setup. This process performs vulnerability scans on network devices, servers and applications to identify vulnerabilities.
Review Security Incident Logs: In this step, the audit process analyzes security logs to identify suspicious activities in your systems and networks. The process prevents unauthorized access to data or eliminates the risk of policy violations. The reviewing process ensures logs are collected, monitored and retained effectively within your organization.
Document Findings and Recommendations: Document the audit findings, such as flaws, vulnerabilities and ways to improve. Give straightforward suggestions on dealing with these problems, ranking them by how dangerous they are and how they might affect people. Therefore, create a report with the results and suggestions for rectifying the vulnerabilities.
Continuous Monitoring: Monitoring the implementation of suggested improvements and regularly reassessing security measures is essential for ongoing cybersecurity work. Thus, create a plan to keep track of progress, deal with problems, and perform regular checks in the future to ensure industry-specific practices.
STRENGTHEN YOUR CYBER DEFENSE WITH CERTPRO
It is important to do a cybersecurity audit, but finding the right external inspector for the job is also essential. An effective audit method can help you find the exact problems. Fixing these problems will help you meet your goals. Costs of auditing are also significant when picking an auditing partner. A well-known company that does privacy audits is CertPro. You can improve the security of your business by following our expert ideas and advice. Our effective methods and ability to find facts also help us determine where the process is weak and vulnerable. The amount of risk and its effect on the business determine how we prioritize the cleanup work. CertPro can do a full safety audit for a price that fits your budget. The possible threats that need immediate attention are our ideas and results.
Furthermore, CertPro streamlines the audit process and offers comprehensive coverage of various security aspects within your organization. So, collaborate with us and unlock the opportunities to perform business safely.
FAQ
What is a cybersecurity audit?
It is a comprehensive review of an organization’s IT infrastructure to identify threats, vulnerabilities, and gaps in security controls, ensuring compliance with industry regulations
How many types of cybersecurity audits are there?
There are two main types: internal audits, conducted by the organization’s employees, and external audits, performed by third-party experts.
Who is responsible for conducting security audits?
It can be conducted by internal IT teams or external auditors, depending on whether the organization opts for an internal or external audit.
What does an audit in cybersecurity include?
It includes risk assessments, reviewing security policies, performing technical evaluations, and analyzing security logs for suspicious activity.
What is an example of a cybersecurity audit in action?
A typical audit involves assessing security policies, conducting vulnerability scans, and testing access controls to identify weaknesses in the system.

About the Author
Shivaprasad Shetty
Shivaprasad Shetty is an ISMS Lead Auditor and Consultant, adept at developing, implementing, and auditing ISO 27001-compliant frameworks. He is also well-versed in SOC 2 compliance, GDPR, HIPAA, and ISO 42001 standards. Shivaprasad excels in ensuring compliance across regulatory frameworks and fostering a secure organizational culture.
IT COMPLIANCE IN 2024: ESSENTIAL TRENDS AND BEST PRACTICES
IT compliance is essential for every organization to secure the integrity and accountability of data. The process also helps develop the business and enhance its profitability. In today’s digital era, IT compliance has more than just a regulatory checkbox. It plays a...
POLICY MANAGEMENT SYSTEM: ESSENTIAL TOOLS FOR AUTOMATION AND SIMPLIFICATION
Growing businesses indicates that you become a master in your field and accurately manage all business-related policies. However, managing company policies can be daunting significantly when your business expands. Here, an effective policy management system can help...
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...




