The National Institute of Standards and Technology developed the framework in 2014 to provide organizations with cybersecurity. Furthermore, NIST CSF is a globally utilized framework for reducing cyber threats. After ten years, NIST has developed NIST 2.0 for its CSF. Therefore, NIST CSF 2.0 is widely used in the cybersecurity framework and is a guiding document for reducing cybersecurity-related risk. The new NIST CSF 2.0 is an updated version that transforms approaches to securing digital assets and infrastructure. Therefore, the evolution significantly impacts managing cyber threats and offers a robust framework for mitigating the digital threat.
This article delved into the key updates regarding the framework and discussed the cybersecurity challenges prompted by the latest version. In addition, we explored the privilege access management and benefits of the NIST framework in today’s dynamic cybersecurity prospect.
WHAT IS NIST CSF?
The NIST cybersecurity framework offers guidelines to help organizations improve their cybersecurity posture and better manage IT security risks. Additionally, it also enhances their protection against cyber threats. The present NIST cybersecurity framework 2.0 aims to improve the cybersecurity landscape and assist the organization in enhancing its cybersecurity posture. In addition, NIST CSF 2.0 offers an innovative platform to facilitate deep and interactive engagement in cybersecurity. Some key features of the framework are discussed below:
Extended the Scope: The main scope of the framework is to focus on protecting critical infrastructure. Thus, it provides the scope of the security control’s guidance to organizations of all sizes and industries.
Improved Clarity and Usability: The NIST CSF 2.0 provides clear guidance that enhances the accessibility of users’ interest in executing the framework.
Focus on Emerging Threats: The new version of NIST CSF addresses contemporary cybersecurity challenges and emerging technological advancements. Hence, it emphasizes cloud security, supply chain management, and threats associated with AI.
Expanded Functionality: The latest version adds a governance function that aims to improve the operational risks and decision-making process. Thus, it helps in the overall implementation of the framework and its effectiveness.
Emphasis on Proactive Evolution: NIST CSF 2.0 emphasizes continuous evolution and improvement in cyber security strategy. Therefore, the framework supports a proactive stance on cybersecurity and encourages organizations to review their cybersecurity practices regularly. Thus, the process helps mitigate potential threats, ensures cybersecurity measures stay aligned with risks, and remains effective over time.
Integration of Privacy and Cybersecurity: The new framework recognizes that privacy and cybersecurity are connected. Again, it ensures that information security is managed based on data and access.
A Focus on Resilience: The NIST Cybersecurity Framework 2.0 takes a forward-looking approach by stressing the importance of creating cyber-resilient systems that allow quick repair from security events.
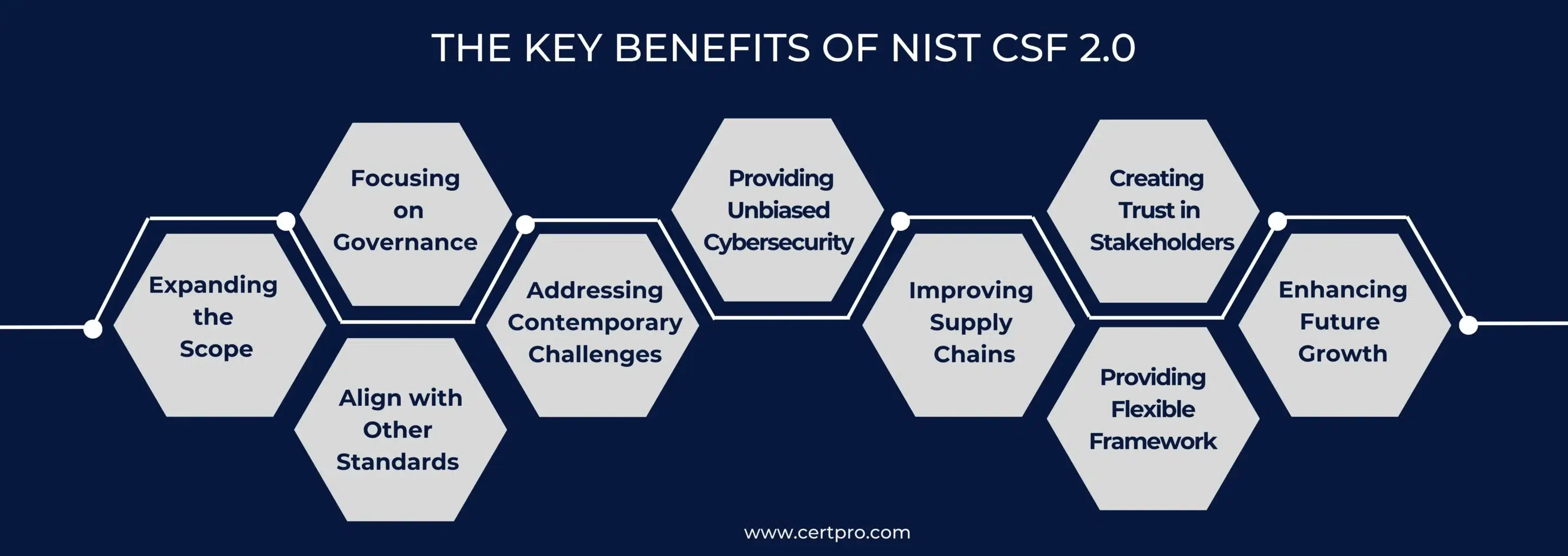
WHAT ARE THE KEY BENEFITS OF NIST 2.0?
The NIST Cybersecurity Framework 2.0 is key to strengthening the overall cybersecurity environment. Similarly, the strategy provides digital security that assists organizations in preventing the risk of data breaches. Here we discuss some more benefits of the NIST CSF 2.0:
Expanding the Scope: NIST 2.0 offers cyber security in critical sectors and small and medium-scale industries.
Focusing on Governance: Governance includes how companies make and carry out well-informed choices about their cybersecurity strategy.
Improving Alignment with Other Standards: NIST CSF 2.0 is aligned with standards like ISO/IEC 27001, helping businesses meet different compliance requirements.
Addressing Contemporary Challenges: NIST 2.0 addresses insider threats, supply chain risk management, third-party risk management, and board cybersecurity control.
Providing Unbiased Cybersecurity: The NIST CSF is a voluntary method that draws on the experience of thousands of information security experts. Generally, It is the best way to do business and the most complete and detailed set of framework controls. Therefore, the main goal of any cybersecurity leader or professional is to protect a company from cyber threats and attacks, and the NIST CSF is an essential part of this task.
Improving Supply Chains: Strategies for managing cyber risks and improving security quickly become essential selling points. Therefore, using NIST CSF helps your business partners trust you, which helps your business grow faster while staying safe.
Creating Trust in Stakeholders: The NIST CSF is based on risk, which leaders fully understand. This method allows you to use a combined cyber risk management technique that fits your company’s goals.
Providing Flexible Framework: CSF 2.0 has the most adaptable structure. Hence, the system has been used successfully by businesses of all sizes, from minor to large-scale industries. Thus, it has a simple function that is easy to understand.
Enhancing Future Growth: Organizations and government bodies that use the Framework are in a much better situation. Thus, it provides a strong security posture for your organization, which will help you grow.
PRIVILEGED ACCESS MANAGEMENT (PAM) AND IDENTITY AND ACCESS MANAGEMENT (IAM) IN NIST
The latest version of NIST CSF 2.0 focuses on IAM and PAM to underpin your organization’s security posture. In addition, IAM ensures the authorization of access to resources for the appropriate reasons. It guarantees secure interaction with systems and data. Thus, the IAM solution can manage user rights and permissions in diverse systems. Therefore, prioritizing IAM can help manage digital identities and prevent data breaches and non-compliance risks.
Meanwhile, PAM plays a critical role in controlling and auditing access privileges. If cyber thieves had access to a privileged account, they could access private data and manipulate it. In this regard, the PAM solution mitigates the risk by implementing privilege principles and authentication measures to verify the identities of those requesting access. It helps the financial sector to identify the vulnerabilities and risks of cyber attacks. In addition, it limits the chances of successful cyber attacks by improving access control of privileged accounts. Similarly, it simplifies the compliance process by automating the whole process.
HOW CAN YOUR ORGANIZATION GAIN NIST COMPLIANCE?
The NIST cybersecurity framework for small companies was created to understand, control, and lower cyber risks. It includes finding, handling, and recovering from cyber threats. Likewise, many organizations now use the NIST cybersecurity framework to educate and inform people inside their groups about cybersecurity management methods, rules, and best practices. If your company is one of the thousands that do business with the data, this plan could be a beneficial starting point. However, different organizations will need different amounts of time to adopt the framework. However, your organization needs to have a plan in place no matter how long it takes, whether a few weeks or years.
WHAT IS THE IMPACT OF NIST CSF 2.0 ON SMALL BUSINESSES?
No one likes having to deal with hacking. It can be done and is much easier than you think. Small businesses must ensure all rules and policies align with the NIST safety standard framework. The Framework is based on standards, regulations, and best practices that are already in place to help companies better control and lower cybersecurity risk. Hence, it helps organizations control and lower risks and improves communication between internal and external stakeholders by giving a way to talk about risk in a business setting. Moreover, NIST provides the framework and credentials to keep the business safe, more robust, and ahead of the following compliance squeeze.
The Framework helps businesses understand, handle, and lower their online risks. Thus, you can decide where to invest in increasing business opportunities. It helps people inside and outside the company talk to each other about cybersecurity risk management by giving them a shared language to use. That means making it easier for people in IT, planning, running units, leaders, customers, and suppliers to talk to each other, share information, and understand each other better.
MAKE NIST CSF 2.0 COMPLIANCE WITH CERTPRO
Implementing NIST CSF 2.0 helps in cybersecurity and protects against cyber threats. Therefore, CSF 2.0 adds essential improvements such as the “Govern” function and a stronger focus on supply chain risk management. It gives organizations a more complete and flexible framework to help them deal with the constantly changing cybersecurity landscape. Moreover, CSF 2.0 can be used by organizations of all kinds and fields. It encourages more open approaches to cybersecurity.
CertPro understands cybersecurity will continue to be a critical priority for organizations worldwide. Thus, with the increasing sophistication and frequency of cyber threats, we offer you compact services in implementing NIST CSF 2.0 in your organization. We assure you that our effort will protect your assets and maintain the trust of the stakeholders.CertPro’s NIST cybersecurity experts have sufficient knowledge and skills in this field. We’ve skilled professionals to guide you in the implementation process. For more details and explanations, visit CertPro.com and get our expert guidance.
FAQ
Is NIST CSF 2.0 mandatory?
It is not mandatory for private businesses; it is a voluntary option to ensure cyber threats. However, NIST CSF is required for federal agencies and their supply chain partners.
Is NIST CSF 2.0 a risk assessment?
It helps in cyber risk management. However, it has also been applied as a strategic planning tool to assess cybersecurity risks in current practices.
How many controls are in NIST CSF?
NIST CSF has five core functions subdivided into 22 categories and 98 subcategories of security controls.
What are the objectives of NIST CSF?
The main goal is prioritizing cybersecurity and incorporating risk assessments into organizational decisions.
What are the 5 pillars of NIST CSF?
The framework has five pillars: identify, protect, detect, respond, and recover.

About the Author
SUBBAIAH KU
Subbaiah Ku is the Regional Director for CertPro in Oman, bringing a wealth of expertise in process and system auditing. As a seasoned lead assessor, Subbaiah is dedicated to ensuring the highest standards in compliance and security. His unique blend of technical acumen, rooted in Mechanical Engineering, is complemented by a diverse range of certifications and extensive training.
IT COMPLIANCE IN 2024: ESSENTIAL TRENDS AND BEST PRACTICES
IT compliance is essential for every organization to secure the integrity and accountability of data. The process also helps develop the business and enhance its profitability. In today’s digital era, IT compliance has more than just a regulatory checkbox. It plays a...
POLICY MANAGEMENT SYSTEM: ESSENTIAL TOOLS FOR AUTOMATION AND SIMPLIFICATION
Growing businesses indicates that you become a master in your field and accurately manage all business-related policies. However, managing company policies can be daunting significantly when your business expands. Here, an effective policy management system can help...
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...




