Technological advancements have also touched healthcare systems and improved ancient medical practices. Today, doctor visits, patient checkups, bills, and keeping health data are digital. In this way, technology is changing medical services and making them more vulnerable to cyber threats. Since 2015, the number of data breaches in the healthcare field has gone up. Evidence showed that the healthcare industry had the most data breaches from 2015 to 2023. In the same way, 2015 was a challenging year for the healthcare industry because more than 112 million patient data were exposed. Thus, healthcare cybersecurity is critical to protecting patient information and continuing businesses.
This article will discuss healthcare cybersecurity in depth, including why it is essential, how to identify threats, and the laws that govern it. Finally, we will look at the best practices of healthcare cybersecurity and the future of cybersecurity. Thus, read the article to learn more about healthcare cybersecurity practices.
WHAT IS HEALTHCARE CYBERSECURITY?
Healthcare cybersecurity measures are tools and strategies for maintaining patient safety. Cybersecurity in healthcare prevents unauthorized access to patient data. Therefore, security measures protect the healthcare sector from cyber threats and reduce the risk of data breaches. In addition, the process protects patient data from human errors or internal threats.
The cybersecurity measures provide email security in healthcare sectors. In healthcare facilities, most of the documentation is transferred through email. Thus, the healthcare sector needs to implement authorization for access to data. In healthcare cybersecurity, physical security measures prevent unauthorized access to dedicated networks. Sometimes, healthcare facilities have legacy systems that need to be supported by current applications. Thus, cybersecurity in the healthcare sector upgrades such systems to strengthen privacy.
WHY IS CYBERSECURITY IMPORTANT TO HEALTHCARE?
Healthcare facilities use technology for many purposes, like diagnosis, recommendations, and data-keeping. Therefore, healthcare cybersecurity aims to establish a standard for finding possible threats and devising a way to mitigate them. Businesses know safety is a reasonable way to build a reputation in today’s market. Let’s talk about why cybersecurity is essential in healthcare.
Protect Patient Information: Healthcare cybersecurity aims to protect patient’s personal information from unauthorized access. The hackers targeted healthcare facilities’ Protected Health Information (PHI) and Personally Identifiable Information (PII). Thus, cybersecurity measures concentrate on these two segments to protect the data.
Provide Competitive Advantages: Implementing a cybersecurity framework in healthcare facilities improves the organization’s reputation and creates customer trust. Businesses need clients’ trust to continue the operational process. Similarly, the security framework helps develop business relationships and provides confidence to stakeholders.
Ensure Continuity of Services: Execution of cybersecurity measures ensures the continuity of work even after the cyberattacks. The incident of data breaches cannot stop the operation if the organization follows security protocol. Organizations cannot prevent cyberattacks in this fragile digital era, but security protocols can minimize their impacts. Thus, implementing hardware failover, restore process, and data backup systems can help in operational continuation.
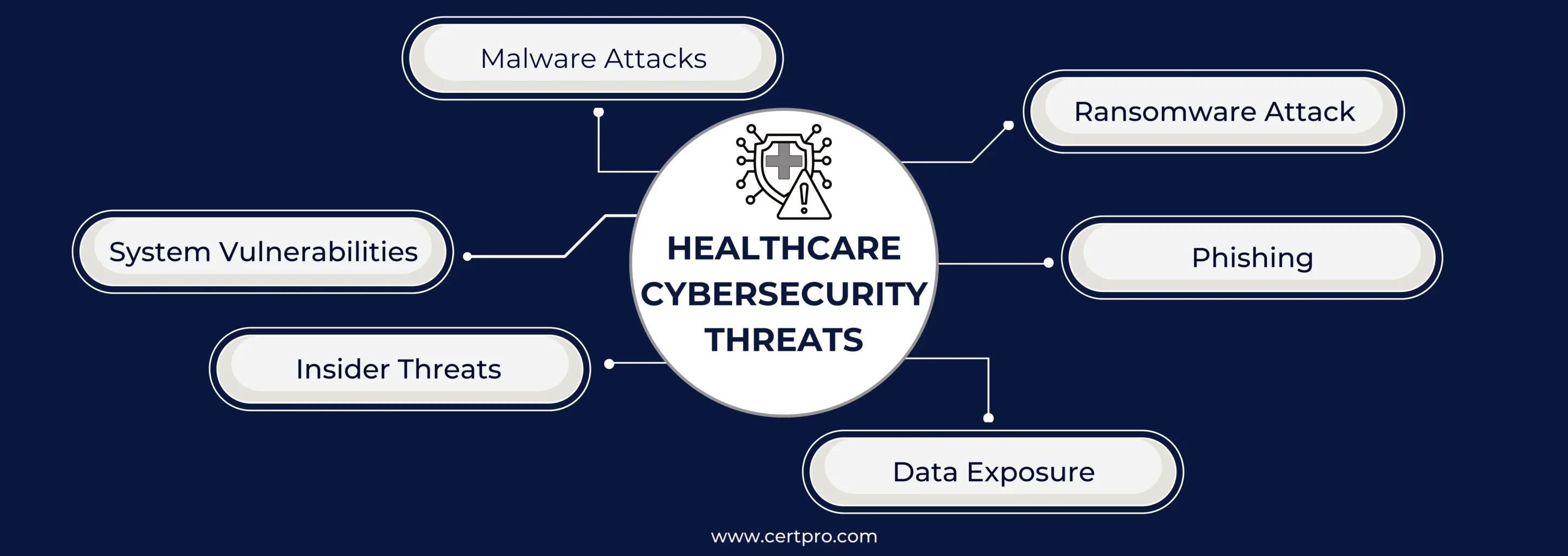
UNDERSTANDING THE HEALTHCARE CYBERSECURITY THREATS
Healthcare organizations are getting constant cyber threats that make their operation difficult. Nowadays, attackers are using multiple techniques; let’s discuss them in brief:
Malware Attacks: Malicious software allows attackers to enter secure systems, steal credentials, collect sensitive data, or take control of the data. These attacks can cause functional disruption in your organization.
Ransomware Attack: This is a special kind of malware designed to encrypt data. The process encrypts the actual file, and hackers take control of the data. In this process, the hackers ask for ransom from the organization to access their data. Therefore, healthcare sectors must have a proper backup of data to avoid such demands. The hackers force the organization to pay the ransom; otherwise, the organization can suffer operational disruption.
Phishing: Cyber-attack techniques that trick users into sharing sensitive information. In this process, hackers might send emails with malicious links or technical terms to convince employees to share their usernames and passwords. Successful phishing attacks allow hackers to access sensitive data and implant malware in the systems. If the phishing attack succeeds, the attackers can access the system, exfiltrate data, plant malware, or execute ransomware.
Data Exposure: It is not an attack, as hackers are not responsible for it. It occurs when poor physical security or IT breaches make sensitive data accessible to unauthorized access. However, the exposure of sensitive data is similar to cyber threats and requires consideration.
Insider Threats: Employees are crucial in maintaining cyber hygiene. Therefore, accidental misuse of data makes it vulnerable. In this scenario, healthcare cybersecurity measures eliminate such risk factors. The measures ensure system configuration and data access controls.
System Vulnerabilities: Out-of-date software, unpatched software, and recalled devices increase the risk of system vulnerabilities. In many countries, information about vulnerable systems is often published in a public database. Therefore, hackers can easily exploit susceptible systems and implant malware. Thus, healthcare cybersecurity updates all the backdated systems and software to avoid the consequences.
BEST PRACTICES IN HEALTHCARE CYBERSECURITY
Healthcare cybersecurity risks and requirements are different for every healthcare organization. However, we are mentioning standard practices for your understanding:
Achieving Visibility: It means knowing about all assets connected to your organization’s network. In a broad aspect, it includes data collection, storage, and access. Therefore, visibility ensures that you are aware of vulnerabilities in your systems. This way, you have a complete view of assessing vulnerabilities, identifying potential risks, and monitoring threats.
Performing Risk Assessments: A risk assessment systematically evaluates the weaknesses and threats in healthcare cybersecurity protocols. Therefore, organizations can use risk assessments to review their controls and find vulnerabilities. Healthcare businesses should perform risk assessments at least once a year as part of their security plan. In addition, regular risk assessments help them meet compliance standards.
Implementing Security Controls: Security controls are the tools that make systems less vulnerable and lower the hacking risks in healthcare industries. Implementing antivirus software as an essential security step can prevent malware threats in your systems. In addition, ransomware attacks can damage your data, but data backup and restore tools can help you continue the business. Therefore, data encryption, network firewalls, crisis reaction plans, and multi-factor authentication are other security measures that healthcare systems can use to protect themselves from cyber threats.
Zero Trust Strategy: Zero trust is a core cybersecurity strategy in healthcare cybersecurity prospects. It reduces unnecessary permissions of control access to healthcare systems. The process can be applied to services, devices, and data assets to restrict communication and mitigate the risk of breaches. Many hospitals are using network access control to monitor their networks and services.
Employees Training: Cybersecurity awareness training ensures that healthcare workers know the risks associated with their work. It confirms that employees follow a strict protocol while handling and managing patient data. In addition, it educates them about identifying phishing emails and their response to suspicious emails. Hence, employees’ awareness can eliminate the risk of internal and external threats.
HEALTHCARE CYBERSECURITY LAWS AND REGULATIONS
Health Insurance Portability and Accountability Act (HIPAA):
HIPAA is a well-known regulation that enforces best practices for healthcare sectors. Following these rules can keep private data safe and secure. The US law says that medical information must be secured from unauthorized access. Healthcare organizations must follow explicit rules set by HIPAA whenever dealing with patient data. The rules provide technology safeguards, physical safeguards, and administrative safeguards. Therefore, the HIPAA privacy rules offer disclosure of protected health information, a form of individually identifiable health information. In addition, the Data Breach Notification Rule ensures that the concerned individual must get notification following a breach of protected health information.
European Union General Data Protection Regulation (GDPR):
Organizations that process personal data from the European Union must comply with the regulation. It provides customers with the right to access their data. GDPR is broader than HIPAA and regulates any information used in the European Union. However, GDPR applies to many types of personal information, whereas HIPAA is concerned about healthcare information.
Personal Information Protection and Electronic Documents Act (PIPEDA):
Private organizations in Canada that handle and manage personal information for business purposes must follow PIPEDA. In some cases, PIPEDA applies to healthcare sectors in Canada. The law protects the patient’s personally identifiable information in medical treatment.
THE FUTURE OF HEALTHCARE CYBERSECURITY
Healthcare cybersecurity will be challenging and becoming more critical than ever. Thus, emerging threats are influencing businesses to find reliable technology partners and consultants who can help them build stronger defenses. Many companies lack cybersecurity experts, which creates difficulties in planning, implementation, and management. In this regard, CertPro can help you implement healthcare cybersecurity regulations with our expert guidance and recommendations. Our customized services reduce your compliance burden and streamline the operational process. Therefore, you can trust CertPro; we will help you implement the correct controls at affordable prices. For more details, visit CertPro.com; our executives will guide you.
FAQ
What is cybersecurity in medical technology?
The medical devices and networks used in medical practice can only partially be secured. Sometimes, medical devices are used as a vector to penetrate network systems. Thus, cybersecurity ensures the safety of the network and devices.
Why is healthcare targeted for cyberattacks?
Hackers can easily manipulate medical devices to control the data. Unfortunately, most hospitals cannot keep security up to date because of multiple gadgets and massive operation systems. Thus, hackers could get into any of their networks, and data violations can occur.
What are the ISO guidelines for cybersecurity?
ISO 27032 is an internationally recognized standard for cybersecurity in healthcare sectors. The standards defend against cyber attacks and manage the risks associated with technologies.
What are the 5 C's of cyber security?
The five Cs are Change, Compliance, Cost, Continuity, and Coverage. The components provide a robust framework for safeguarding the business goals.
What are the 4 cybersecurity protocols?
The protocols are encryption, authentication, intrusion detection, and firewall management. These protocols collectively contribute to a multi-layered defense against cyber threats.

About the Author
Shivaprasad Shetty
Shivaprasad Shetty is an ISMS Lead Auditor and Consultant, adept at developing, implementing, and auditing ISO 27001-compliant frameworks. He is also well-versed in SOC 2 compliance, GDPR, HIPAA, and ISO 42001 standards. Shivaprasad excels in ensuring compliance across regulatory frameworks and fostering a secure organizational culture.
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...
BUSINESS NON-COMPLIANCE: THE HIDDEN FINANCIAL AND OPERATIONAL COSTS
Businesses are always in a dilemma regarding whether or not to be compliant. Most companies think that compliance will problematize their operating process. However, highly regulated industries like financial and healthcare services meet the legal obligations for...
Security Frameworks: A Comprehensive Guide with 14 Examples
Technological advancements make cyberattacks more sophisticated and advanced. Hence, organizations must keep up with the latest cybersecurity frameworks in these complicated scenarios to sustain themselves in a dynamic threat environment. Different cybersecurity...
NAVIGATING DATA PRIVACY FRAMEWORKS: A COMPREHENSIVE GUIDE
Globalization has intense effects on business functioning and scaling. In today's digital world, companies are generating an unprecedented rate of data that requires protection from emerging cyber threats. In addition, recurring data breaches and privacy concerns make...
BUSINESS NON-COMPLIANCE: THE HIDDEN FINANCIAL AND OPERATIONAL COSTS
Businesses are always in a dilemma regarding whether or not to be compliant. Most companies think that compliance will problematize their operating process. However, highly regulated industries like financial and healthcare services meet the legal obligations for...
Security Frameworks: A Comprehensive Guide with 14 Examples
Technological advancements make cyberattacks more sophisticated and advanced. Hence, organizations must keep up with the latest cybersecurity frameworks in these complicated scenarios to sustain themselves in a dynamic threat environment. Different cybersecurity...




